
With organizations increasingly facing diverse and sophisticated cyber threats, many lack either the tools, in-house expertise, or both to effectively counter them. As a result, many organizations are now turning to Security Operations Centers (SOCs)—whether outsourced or in-house—for their cybersecurity needs. A SOC can handle a broad range of cyber threats, from novice hackers and malicious insiders to organized cybercrime groups and nation-state threat actors.
Accompanying this trend is an increased demand for SOC analysts. In this comprehensive guide, you’ll learn what a SOC analyst is, what they do, how much they earn, and how to become one. The information we’ve shared in this guide can help you determine if a SOC analyst profession is a suitable career path for you.
What is a SOC Analyst?
A SOC analyst is a professional who takes part in the daily functions of a SOC, a centralized command center dedicated to detecting, analyzing, responding to, and reporting malicious network activity. SOC analysts work as a team to protect an organization or organizations from cyber threats and to neutralize any detected threats in the shortest possible time.
Once you become a SOC analyst, you’ll play a critical role in driving a SOC’s performance, efficiency, and effectiveness in safeguarding an organization’s or organizations’ IT assets and infrastructure. To give you a glimpse of how a day in the life of a SOC analyst looks like, let’s discuss an analyst’s key roles and responsibilities.
Key roles and responsibilities – What does a SOC analyst do?
A SOC analyst’s day-to-day activities primarily involve detecting, analyzing, responding to, defending against, and reporting on cyber attacks. Thus, we can classify their roles and responsibilities into three distinct phases—before, during, and after a cyber attack.
Before a cyber attack
- Set up security controls
- Enforce security policies
- Harden systems to minimize or completely get rid of vulnerabilities
- Monitor the network for suspicious activities
- Participate in drills that simulate attack and defense scenarios to hone incident response capabiltiies as well as measure how fast the SOC detects and neutralizes threats
During a cyber attack
- Review alerts generated by tools that detect cyber threats
- Identify a cyber attack through indicators of compromise (IOCs), such as known malicious IP addresses, file hashes, unauthorized elevation of user privileges, etc.
- Block identified malicious traffic
- Contain the threat and prevent it from affecting other systems
- Help minimize cyber threat dwell time or the duration in which a threat persists undetected in a network
- Collect artifacts during incident response so they can be used as references during forensic investigation
- Ensure adherence to internationally recognized standards and procedures in case the artifacts are used in legal proceedings
After a cyber attack
- Determine the scope of the incident. Identify what systems have been compromised and affected
- Remediate affected system
- Restore affected systems to a known good state
- Institute measures to mitigate the risk of re-occurrence
- Collaborate with other departments, such as IT, Legal, and HR, before, during, and after a cyber incident to defend against as well as mitigate impact of a cyber incident.
The specific SOC analysts in charge of the tasks enumerated above largely depend on their respective experience and skillsets, which can be classified in tiers.
Differences between SOC Analyst Tiers
SOC analysts are usually classified into four tiers: Tier 1, Tier 2, Tier 3, and Tier 4. Analysts on each tier have their own set of responsibilities, which contribute to the effectiveness of the SOC. By familiarizing yourself with the unique functions of each tier, you’ll know what you’re expected to do if assigned to one of these tiers.
Different SOCs may assign additional sets of responsibilities for each tier, but, in most cases, the responsibilities associated with each tier look like this:
Tier 1: Triage Specialist
In this entry-level SOC analyst role, your primary responsibility is to review alerts and determine whether the incidents associated with them are real issues or just false positives. If an alert is legitimate, you’re supposed to escalate the incident to a Tier 2 analyst. It’s important that you get your triaging right so that other members of your SOC won’t waste time dealing with false alarms.
Tier 2: Incident Responder
As a Tier 2 SOC analyst, your job is to handle confirmed incidents. First, you’ll need to conduct a thorough assessment to determine the scope of the attack and identify any systems, applications, or data that might be affected. Next, you’ll need to implement containment and remediation until the threat is neutralized.
If the threat is indeed neutralized, you should document the incident for future analysis or reporting. However, if you suspect that the threat still persists in your environment, you may escalate the issue to a Tier 3 analyst.
Tier 3: Threat Hunter
The analysts who occupy this position have a more advanced skill set than their Tier 1 and Tier 2 colleagues. In this role, you’ll typically take over incident response duties that Tier 2 analysts can’t handle. In addition, you may also have to hunt for threats that may have slipped past your detection tools. These threats may include Advanced Persistent Threats (APTs) and Zero-days.
Tier 4: SOC Manager
The SOC manager is the leader of the team. If you’re promoted to this role, you’ll supervise team members and coordinate their actions to ensure a seamless operation. In addition, you may also have to:
- Coordinate incident response efforts and ensure proper escalation and resolution of threats
- Conduct regular performance reviews for your team of analysts and provide guidance for professional growth
- Develop and enforce standard operating procedures (SOPs) and playbooks for efficient incident handling
- Collaborate with other departments, such as IT, HR, GRC (Governance, Risk, and Compliance), legal, and public relations to address security risks, ensure regulatory compliance, and contact external entities for post-breach activities
SOC analyst tools
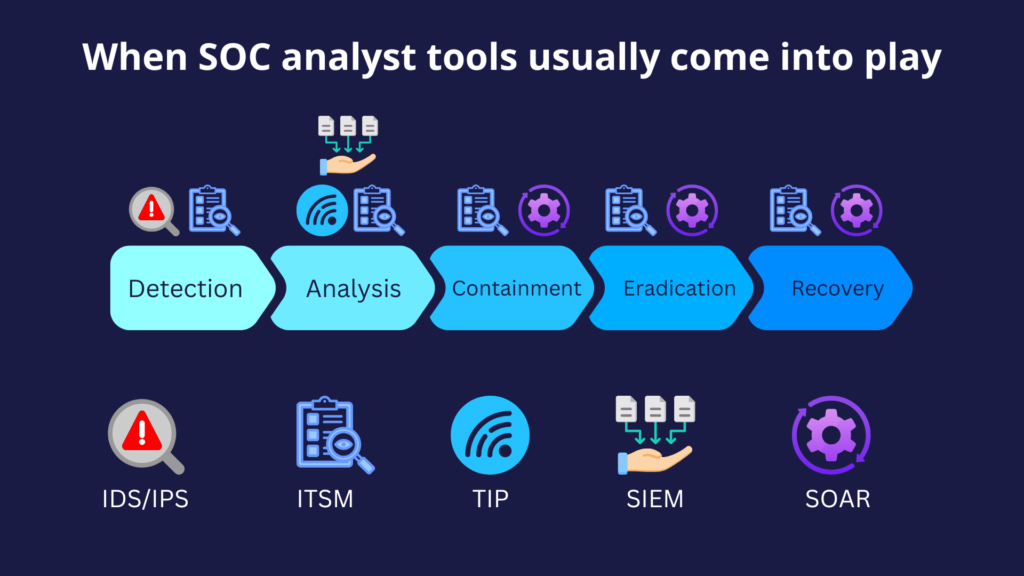
SOC analysts rely on a wide range of tools to detect, analyze, and respond to cybersecurity threats effectively. Here are some of the most essential tools you’ll encounter should you become a SOC analyst:
IT Service Management (ITSM)
ITSM platforms like ServiceNow, Jira Service Management, and Freshservice enable SOC teams to manage, document, and streamline incident handling processes. These tools are integral to SOC workflows since they ensure incidents are logged, prioritized, and tracked from detection to resolution.
For example, if you’re a Tier 1 or Tier 2 SOC analyst and you need to escalate an issue to a Tier 2 or Tier 3 analyst, you would typically do that through an ITSM. All updates pertaining to that issue can be added, viewed and tracked in one place.
Security Information and Event Management (SIEM)
Often regarded as the cornerstone of a SOC, a SIEM serves as the central hub for monitoring, detecting, and analyzing security events. SIEMs like Splunk, IBM QRadar, and Exabeam LogRhythm aggregate and analyze logs from across an organization’s IT infrastructure to identify patterns indicative of malicious activity.
Without them you would have to manually collect and review log data from disparate sources such as firewalls, endpoints, servers, and applications—a time-consuming and error-prone process that lacks the correlation and automation capabilities necessary for effective threat detection and response.
Intrusion Detection and Prevention Systems (IDS/IPS)
IDS/IPS tools such as Snort, Suricata, and Cisco Firepower monitor network traffic to detect and block malicious activities, such as brute force attacks or malware communications. When you use an IDS/IPS tool in a SOC environment, you typically integrate it with a SIEM. The SIEM ingests the alerts that the IDS/IPS generates and correlates them with other alerts coming from other security tools.
Threat Intelligence Platforms (TIPs)
Threat intelligence platforms such as Recorded Future, ThreatConnect, Mandiant gather and analyze information on current and emerging threats as well as Indicators of Compromise (IOCs), such as malicious IPs, domains, and file hashes. TIPs help you stay ahead of attackers by providing actionable intelligence, so you can quickly identify and respond to threats.
Security Orchestration, Automation, and Response (SOAR)
To automate repetitive tasks and orchestrate response workflows, many SOCs employ SOAR platforms such as Palo Alto Cortex XSOAR, Splunk Phantom, and IBM Resilient. SOAR tools reduce response time by automating tasks such as log analysis, threat hunting, and incident response playbook execution. While a SIEM reduces the number of screens you have to review when analyzing or responding to an incident, a SOAR reduces the number of tasks you need to perform.
How much does a SOC analyst make?
SOC analyst salary ranges can vary depending on several factors, with location and experience level being two of the most significant determinants. Here are some rough estimates of the salary ranges you can find in different countries. For more accurate and up-to-date information, you can check salary research platforms, such as Glassdoor, PayScale, and Indeed.
| Location | Average (annual) salary range (USD) | ||
| Entry-level | Mid-level | Senior-level | |
| United States | $55,000 – $80,000 | $80,000 – $110,000 | $110,000 – $150,000 |
| Australia | $50,000 – $75,000 | $75,000 – $100,000 | $100,000 – $130,000 |
| United Kingdom | $45,000 – $65,000 | $65,000 – $85,000 | $85,000 – $115,000 |
| United Arab Emirates | $40,000 – $60,000 | $60,000 – $85,000 | $85,000 – $120,000 |
| South Africa | $20,000 – $35,000 | $35,000 – $50,000 | $50,000 – $70,000 |
| India | $8,000 – $15,000 | $15,000 – $25,000 | $25,000 – $40,000 |
How to become a SOC analyst
Becoming a SOC analyst is an exciting pathway for individuals who are not just passionate about cybersecurity, but really want to be in the thick of battle and actively protect organizations from cyber attacks. To achieve this role, you’ll need to build a solid foundation consisting of education, skills, certifications, and hands-on experience.
1. Educational foundation
As of this writing, we couldn’t find any degree dedicated specifically for aspiring SOC analysts. While a formal degree isn’t mandatory for becoming a SOC analyst, it can significantly improve your chances of landing a role. Many SOC analysts have a bachelor’s degree in fields such as:
- Computer Science
- Information Technology
- Cybersecurity
If pursuing a formal degree isn’t an option, you might want to consider taking specialized cybersecurity programs, online courses, or boot camps. Websites like Coursera, edX, and Udemy offer beginner-friendly options to learn essential for SOC analysts. One example is Cisco’s Cybersecurity Operations Fundamentals Specialization at Coursera.
2. Certifications
Employers typically seek concrete evidence of your proficiency in SOC-related tasks. While a degree in fields like cybersecurity, information technology or computer science is ideal, relevant certifications can be an excellent alternative for those without formal education in these areas.
In fact, given that degree programs specifically tailored to SOC analyst roles are not widely available, certifications from well-established industry organizations are often more highly valued. Some of the most recognized certifications include:
- Cisco Certified CyberOps Associate
- Certified SOC Analyst (CSA)
- GIAC Security Essentials (GSEC)
- GIAC Certified Incident Handler (GCIH)
- Splunk Core Certified User
- ComTIA Security+
If you have no experience in either cybersecurity or cloud computing, you can use these professional certificate programs at Coursera as jump-off points:
- Google Cloud Cybersecurity Professional Certificate
- Microsoft Cybersecurity Analyst Professional Certificate
- IBM Cybersecurity Analyst Professional Certificate
- IBM and ISC2 Cybersecurity Specialist Professional Certificate
- Cisco’s Cybersecurity Operations Fundamentals Specialization
We wrote overviews of those first four certificate programs in our blog post: 4 Coursera Cybersecurity Courses with Professional Certs for Beginners.
3. Relevant Skills
To excel as a SOC analyst, you need to master both technical and soft skills. You’ll need technical skills to handle security tools and affected systems, as well as write code to automate tasks. On the other hand, you’ll also need soft skills to think out of the box and work with other people, some of whom may not be well-versed in cybersecurity or IT.
Technical Skills
- Network Fundamentals: Knowledge of TCP/IP, subnets, and firewalls
- SIEM Tools: Expertise in platforms like Splunk, QRadar, or Exabeam to monitor and analyze security events
- Endpoint Detection and Response: Proficiency with tools like CrowdStrike, SentinelOne, or Carbon Black
- Operating Systems: Familiarity with security-focused Linux distributions (e.g., Kali Linux, Security Onion) and Windows environments
- Threat Detection: Ability to identify IOCs and use threat intelligence platforms
- Scripting: Basic knowledge of Python, Bash, or PowerShell for automation and analysis.
Soft Skills
- Attention to Detail: Critical for analyzing logs and identifying subtle signs of malicious activity
- Communication: SOC analysts often need to report findings to non-technical stakeholders
- Team Collaboration: SOC work involves coordinating with other analysts and teams during incidents.
4. Experience
Hands-on experience is crucial for landing a SOC analyst role. More often than not, employers will value experience more than any other criteria. Here’s where you can gain relevant experience if your’re still new to this field:
Entry-Level Roles
Start with positions like IT support, help desk technician, or junior cybersecurity analyst. These roles build foundational knowledge in system monitoring, troubleshooting, and basic security practices. Sometimes, you even get to tackle security-related incidents. For instance, when I worked as a tech support engineer at JSCAPE, I learned how to indentify DDoS attacks or brute force attacks from server logs.
Internships and Apprenticeships
Many organizations, especially MSSPs (Managed Security Service Providers), offer SOC internships. These are excellent opportunities to gain practical, real-world experience with SIEM tools and incident response processes.
Cybersecurity Labs and Simulations
Platforms like TryHackMe, Hack The Box, and Cyber Ranges offer simulated environments where you can practice detecting and mitigating threats. Many of these platforms provide guided learning paths specifically for SOC analysts.