In cybersecurity, it’s better to prevent a threat than to react to it once it’s already inside your network. Today’s most effective security teams try to anticipate threats by tracking adversaries, gathering intelligence, and sharing insights across the organization before an attack occurs.
That’s where Cyber Threat Intelligence (CTI) comes in. And at the heart of CTI efforts are Cyber Threat Intelligence Analysts.
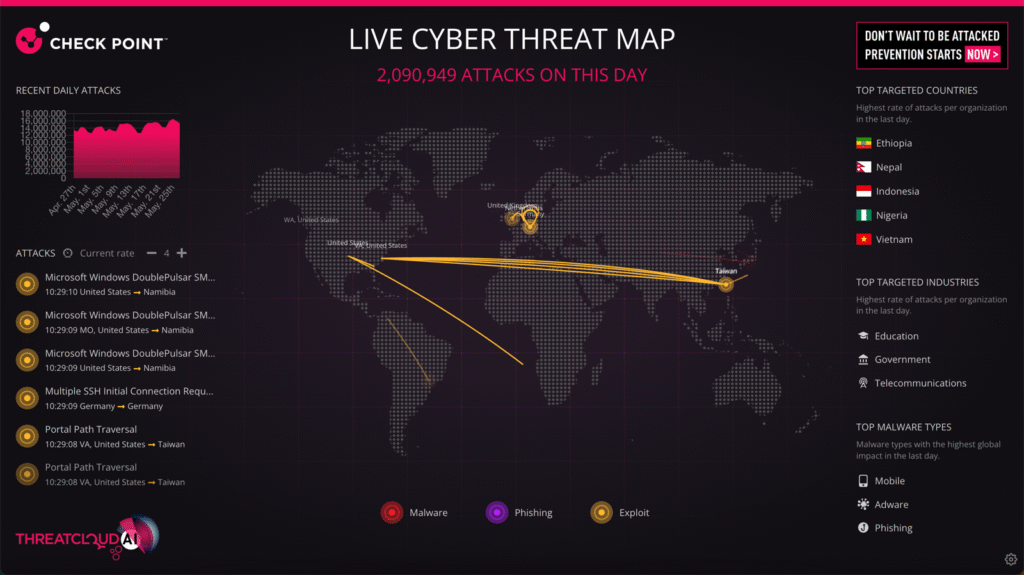
These analysts help organizations make sense of a noisy, complex threat landscape. They translate raw data (ranging from open-source indicators to dark web chatter) into actionable intelligence. This intelligence then informs decisions across the security stack, from fine-tuning detection rules to preparing for emerging attack techniques.
In this article, we’ll unpack what a Cyber Threat Intelligence Analyst actually does, what skills and tools they use, and what path you can take if you’re interested in becoming one.
What is a Cyber Threat Intelligence Analyst?
A Cyber Threat Intelligence Analyst is someone who studies the behavior, motives, and tools of cyber attackers, and then turns those insights into something an organization can act on.
Unlike a SOC analyst who monitors for threats in real time, or an incident responder who reacts after something goes wrong, a CTI analyst works further upstream. Their focus is on understanding the who, what, and why behind attacks—often before those attacks even happen.
CTI analysts sift through data from threat feeds, underground forums, malware samples, and public disclosures to spot patterns. They might investigate how a ransomware gang operates, track a phishing campaign’s infrastructure, or identify new vulnerabilities being discussed on the dark web.
Threat intelligence typically falls into four categories:
- Strategic – High-level summaries intended for executives and decision-makers (e.g., threat trends in a given region or industry).
- Tactical – Information about tools as well as tactics, techniques, and procedures (TTPs) used by threat actors (e.g., a new phishing tactic or malware variant).
- Operational – Insights that can inform incident response (e.g., how an attacker gains initial access or moves laterally).
- Technical – Specific indicators of compromise (IOCs) like IP addresses, file hashes, or domain names.
Good CTI analysts are translators of sorts. They bridge the gap between raw data and meaningful insight, helping defenders prioritize risks, improve detection, and be better prepared for potential attacks.
Key Roles and Responsibilities
The day-to-day work of a Cyber Threat Intelligence Analyst can vary depending on the size and maturity of the organization. But generally, their responsibilities revolve around one core goal: helping the organization stay ahead of cyber threats through intelligence gathering, correlation, and analysis.
Here’s what that often looks like:
1. Gathering Threat Data
CTI analysts spend a good chunk of time collecting data. That might include:
- Monitoring threat intelligence feeds (both commercial and open source)
- Scanning dark web forums or Telegram channels for chatter related to your industry
- Tracking indicators of compromise (IOCs) published in threat reports
- Following adversary behavior frameworks like MITRE ATT&CK
2. Analyzing and Enriching Information
Raw data isn’t all that helpful until it’s processed. Analysts correlate data from multiple sources, validate it, and look for context. The goal of these activities is to answer questions like:
- Who’s behind this threat?
- What tools or infrastructure are they using?
- What vulnerabilities are they targeting?
- How relevant is this to us?
3. Producing and Sharing Intelligence
Once the information is contextualized, CTI analysts tailor their findings for different audiences. A Security Operations Center (SOC) analyst might want to see indicators of compromise (IOCs), while a vulnerability manager may need a CVE (Common Vulnerabilities and Exposures) list prioritized by threat relevance:
| Audience | Deliverables | Purpose | Format / Style |
| Executives | High-level briefings, dashboards, risk summaries | Inform strategic decisions, justify security investments, assess business impact | Concise, visual, non-technical |
| SOC Analysts / Blue Team | IOC lists, detection rules, threat actor profiles | Improve alert accuracy, tune detection systems, enrich investigations | Technical, structured, actionable |
| Incident Response Teams | TTP breakdowns, attack timelines, playbooks | Speed up containment and remediation, support investigation workflows | Detailed, time-sensitive, scenario-based |
| Vulnerability Management | Threat-prioritized CVE lists, exploit data | Prioritize patching, align remediation with real-world threats | CVE-focused, risk-weighted |
| Red Teams / Pentesters | Threat actor emulation plans, real-world TTPs | Simulate adversaries, test defenses, assess resilience | Adversary-informed, technically detailed |
4. Supporting Defensive Efforts
CTI analysts often work closely with:
- Detection engineers to refine Security Information and Event Management (SIEM) and Endpoint Detection and Response (EDR) rules
- Vulnerability management teams to prioritize patching
- SOC analysts to provide context during investigations
- Red teams to simulate adversary tactics
5. Staying Ahead of the Curve
A big part of the role is constant learning. New threat actors, new malware, new techniques—there’s always something emerging. Analysts are expected to keep tabs on the latest developments and understand how they might impact their organization.
Core Skills and Tools
While Cyber Threat Intelligence Analysts collect a lot of data, they must also know what to look for, how to interpret it, and how to turn it into an advantage in cybersecurity operations. That skillset takes a mix of analytical thinking, technical knowledge, and communication skills. It also requires familiarity with a growing set of tools and frameworks.
1. Analytical and Investigative Skills
At its core, threat intelligence is a research role. You need to spot patterns, connect dots, and stay skeptical of surface-level information. The best analysts are naturally curious. They’re the kind of people who read five sources just to verify one detail.
2. Familiarity with Threat Frameworks
You’ll often map attacker behavior to structured models like:
- MITRE ATT&CK – Documents real-world tactics, techniques, and procedures (TTPs) used by threat actors.
- Diamond Model of Intrusion Analysis – A framework for analyzing threats using adversary, infrastructure, capability, and victim as key perspectives.
- Kill Chain Model – Helps analysts understand and disrupt an attack at each stage.
3. Technical Literacy
While CTI isn’t always hands-on keyboard, you do need to understand technical concepts. That includes:
- How malware behaves
- Common vulnerabilities and exploitation methods
- Basic scripting or querying (Python, regex, YARA, STIX/TAXII)
- Familiarity with networking, system logs, and indicators like hashes, domains, or IPs
4. Communication and Reporting
You’ll be translating complex findings into reports tailored to different audiences. That means knowing how to adjust tone, detail, and structure depending on whether you’re briefing a CISO or handing off to a SOC analyst.
5. Tools of the Trade
While tools will vary depending on the organization, here are a few commonly used ones:
- Threat Intelligence Platforms (TIPs) – Recorded Future, ThreatConnect, MISP
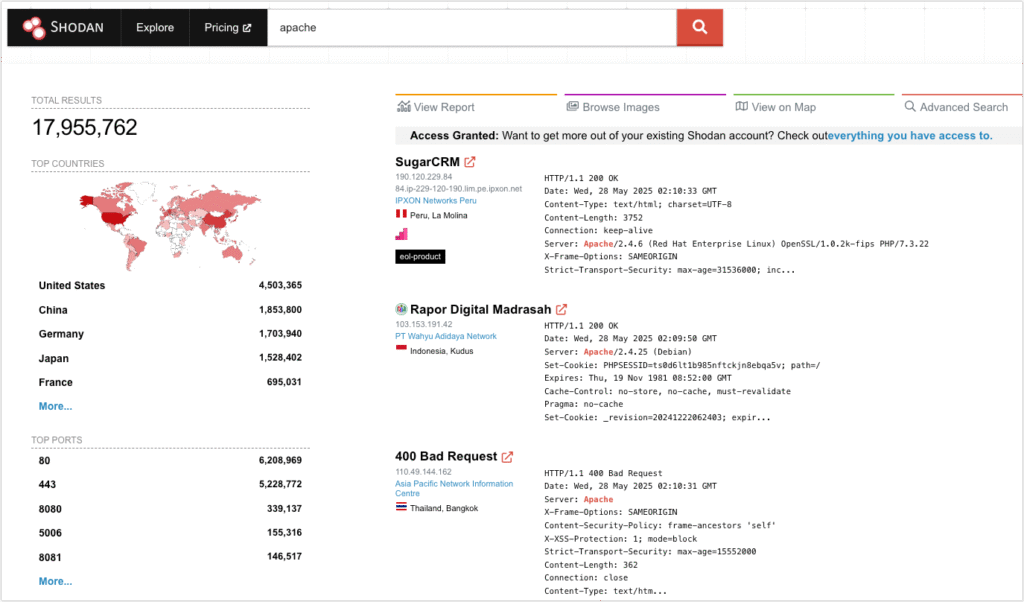
- Open Source Intelligence (OSINT) – Shodan, VirusTotal, GitHub, social media
- Dark Web Monitoring – Tools or services that track underground forums and marketplaces
- Sandboxing and Malware Analysis – Any.Run, Cuckoo Sandbox, Hybrid Analysis
- Threat Feeds and Aggregators – AlienVault OTX, Cisco Talos, abuse.ch
The role is as much about filtering out noise as it is about spotting something new. That’s why strong intuition, built through experience, often separates good CTI analysts from great ones.
How Much Does a CTI Analyst Make?
The table below presents estimated annual salary ranges in USD for entry-level, mid-level, and senior-level CTI analysts across six key regions. These figures are based on data compiled from industry salary surveys and job market platforms such as Glassdoor, PayScale, and Indeed, alongside cybersecurity career reports.
While exact figures can fluctuate due to market demand and company size, this table provides a reliable benchmark for understanding compensation expectations globally.
| Location | Entry-Level | Mid-Level | Senior-Level |
|---|---|---|---|
| United States | $60,000 – $90,000 | $90,000 – $130,000 | $130,000 – $180,000 |
| Australia | $50,000 – $80,000 | $80,000 – $110,000 | $110,000 – $140,000 |
| United Kingdom | $45,000 – $65,000 | $65,000 – $95,000 | $95,000 – $130,000 |
| United Arab Emirates | $40,000 – $60,000 | $60,000 – $100,000 | $100,000 – $140,000 |
| South Africa | $20,000 – $35,000 | $35,000 – $55,000 | $55,000 – $80,000 |
| India | $8,000 – $15,000 | $15,000 – $30,000 | $30,000 – $50,000 |
How to Become a Cyber Threat Intelligence Analyst
There’s no single path into cyber threat intelligence, which is part of what makes it so accessible. Whether you’re coming from IT, security operations, journalism, or even the military, the key is developing a blend of analytical thinking, cybersecurity awareness, and threat-centric curiosity.
1. Build a solid foundation
Most CTI analysts start with a background in cybersecurity, IT, or intelligence analysis (e.g., in military, law enforcement, geopolitics, or even business). A degree in Computer Science, Cybersecurity, Intelligence Studies, or even Political Science (with a security focus) can help, but it’s not a strict requirement. What’s more important is your ability to:
- Understand network protocols and operating systems
- Follow security news and threat actor behavior
- Read technical reports and threat blogs critically
2. Learn to think like an analyst
Practice dissecting cyber incidents. Read breach reports and try to answer: What happened? Who was behind it? Why did defenses fail? What can we learn from it? This type of thinking is the core of threat intelligence.
You can also sharpen your analytical skills by studying:
- MITRE ATT&CK and how different actors use TTPs
- Threat modeling methodologies
- Case studies from reports by Mandiant, Recorded Future, or Microsoft Threat Intelligence
3. Get Familiar with CTI Tools and Platforms
Start by exploring:
- OSINT tools – Shodan, VirusTotal, Censys, Maltego
- Threat feeds – AlienVault OTX, abuse.ch, CERTs, Twitter/X
- Sandbox services – Any.Run, Hybrid Analysis
- TIPs – Try open-source options like MISP to understand how intel is collected and shared
If you’re not in a security role yet, many of these tools are publicly available, and you can experiment with them to build your confidence and showcase your initiative.
4. Earn Relevant Certifications
Certifications aren’t required, but they help demonstrate credibility, especially if you’re switching from another role. Consider:
- GIAC Cyber Threat Intelligence (GCTI) – One of the most recognized in the field
- Certified Threat Intelligence Analyst (CTIA) – Offered by EC-Council
- CompTIA CySA+ – A broader security cert that includes some threat analysis
- MITRE ATT&CK Defender (MAD) – Focuses on applying ATT&CK in real-world scenarios
5. Transition from Related Roles
Many CTI analysts come from adjacent positions like: SOC analyst, incident responder, Malware analyst, cybersecurity analyst, intelligence analyst (e.g., military or law enforcement background). If you’re already in cybersecurity, consider volunteering to help your team with threat research, reporting, or IOC enrichment to build experience organically.
Conclusion
Cyber Threat Intelligence is one of those roles that sits at the intersection of research, technology, and security operations. It doesn’t require you to be the most technical person in the room, but it does require you to be curious, methodical, and good at connecting the dots.
Whether you’re helping a SOC respond faster, giving execs clearer visibility into emerging risks, or assisting vulnerability management teams in prioritizing patching, a CTI analyst plays a key role in strengthening an organization’s security posture.
If you like tracking cyber threats, diving into TTPs, and turning messy, raw threat data into meaningful insight, it’s a role worth looking into.