VPNs and firewalls are two of the most basic cybersecurity tools. Many organizations have at least one of these two. That said, is there any scenario when you would need both? We answer that question and more in this VPN vs firewall article.
Here, you’ll learn what a firewall and a VPN is as well as the pros and cons of using each one. You’ll also learn when you should use a VPN over a firewall and vice versa. Lastly, we’ll discuss if it’s advisable to use them together. Ready? Let’s begin.
What is a Firewall?
A firewall is a security tool that restricts traffic from one network to another or from one portion of a network to another. It’s arguably the most common cybersecurity tool, being installed and enabled by default in Windows machines. In case you’re wondering, it’s the tool that monitors, filters, and controls network traffic to and from your Windows PC or laptop according to predefined security rules.
When used properly, a firewall can prevent external threats from reaching your network or your endpoint device like your PC or laptop. A firewall can also enable you to apply network segmentation, which isolates portions of your network. Network segmentation prevents unauthorized traffic from wandering off into portions of your network that are irrelevant to their business functions.
Types of firewalls
Security, operational, and budgetary requirements normally dictate the type of firewall you’ll need for your organization. The built-in firewall that comes with Windows is a host-based firewall. Other common types of firewalls include the following:
- Packet-filtering firewall – The most basic and affordable type of firewall. Use this firewall for simple filtering use cases.
- Circuit-level gateway – Ideal if you have a limited budget but require something better than packet filtering.
- Stateful inspection firewall – Use this type if your firewall needs require awareness of a packet’s ‘state’.
- Proxy firewall – Use this firewall if you need a tool to inspect deep into a packet and search malicious activity.
- Next Generation Firewall (NGFW) – Best suited for large organizations, use this firewall if you require advanced protection and have deep pockets.
Alright, let’s proceed with the other protagonist in this VPN vs firewall comparison.
What is a VPN?
VPN stands for virtual private network. It’s a private network that operates over a public network like the Internet by using encryption. When you use a VPN, members of your organization can send and receive data through that public network without worrying about eavesdroppers. Eavesdroppers who attempt to intercept your connection can’t extract any meaningful information because the VPN encrypts your data. Although Windows also has a VPN client installed by default, you still need to connect to a VPN server for it to be operational.
A VPN encrypts on a per-link basis, not on a per-application basis the way, say, HTTPS does. With an application-level encryption, you need both the server and client application to support the same encrypted protocol. For example, with HTTPS, both your web server and your web browser need to support HTTPS. With a VPN, any traffic from any application can pass through a VPN and be encrypted. Even your applications that don’t have built-in encryption can benefit from the encryption provided by a VPN.
Types of VPNs
VPNs can be classified by their architecture. What you’ll find below are three commonly used VPN architectures:
- Site-to-Site VPNs
- Remote Access VPNs
- Host-to-Host VPNs
Site-to-site VPNs connect two or more networks through what are known as VPN gateways.
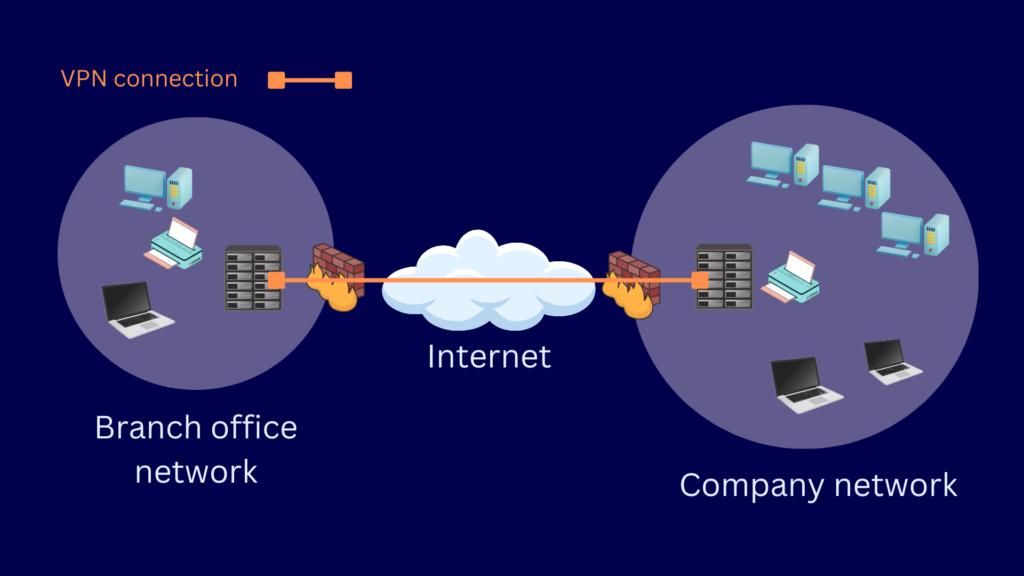
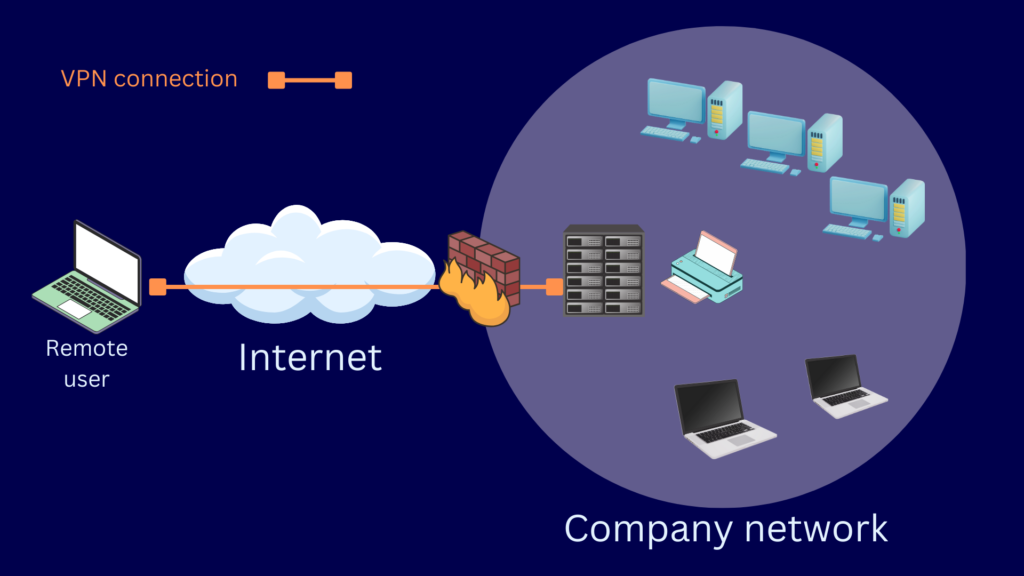
Remote access VPNs connect user-controlled VPN clients to a VPN gateway.
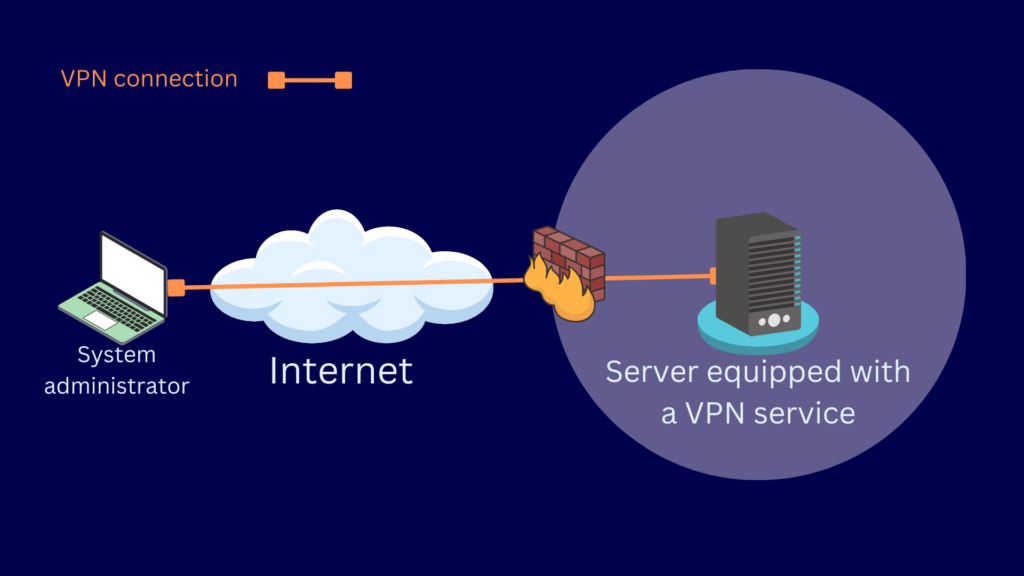
Host-to-host VPNs connect VPN clients directly to a remote server.
We’ve already discussed these three types of VPN architectures in detail in our article on the types of VPNs. Kindly click that link if you wish to read about them.
We can’t make a complete VPN vs firewall comparison unless we discuss the pros and cons of these tools.
Pros & Cons of Firewalls
First, let’s look into the pros and cons of using a firewall. While I’ve outlined an equal number of advantages and disadvantages, I’d like to point out that the advantages far outweigh the disadvantages. A firewall is something you simply can’t do without if you your business relies on any form of IT environment.
Pros of firewalls
- Serves as a first line of defense – Yes, we’re aware of insider threats. Still, most threats originate from outside your network. When deployed at your network perimeter, firewalls can help keep external threats from entering.
- Prevents lateral movement – Insider threats and threat actors that manage to evade perimeter defenses execute lateral movement to reach their targets. Network segmentation can mitigate this maneuver.
- Enables regulatory compliance – Data security laws and regulations like PCI DSS recommend firewalls for meeting certain requirements. Access control and network segmentation, for example, can be achieved by using firewalls.
Cons of firewalls
- Adversely affects performance – Every time a firewall inspects a packet, it delays the transmission of that packet. Worse, if a firewall rule is overly restrictive, some valid packets integral to a business process could end up getting blocked.
- Costs money – While some firewalls cost lest than $100, the more advanced and more capable firewalls can exceed $100,000. If you’re running a small business, it’s important to choose a firewall that matches your needs and budget.
- Requires expert engagement – To avoid overly or inadequately restrictive rulesets, your firewall admin must be well-versed with your security, IT, and business requirements. A person with this level of competency won’t be easy to find.
Since we’re comparing VPN vs firewall, let’s talk about VPN pros and cons as well.
Pros & Cons of VPNs
Like a firewall, a VPN can also be a significant investment. It’s therefore important to make sure you understand the pros and cons of using one.
Pros of VPNs
- Thwarts man-in-the-middle attacks – Man-in-the-middle attacks intercept network connections to steal sensitive data like usernames and passwords. A VPN thwarts these attacks by rendering data unreadable.
- Improves trading partner confidence – Many B2B data exchanges require a high level of confidentiality. By supporting VPN-protected B2B exchanges, you can reassure trading partners of your transaction’s security.
- Enables regulatory compliance – Data security laws and regulations like PCI DSS mandate the use of encryption when transmitting data over public networks. The encryption capabilities of a VPN make it suitable for this purpose.
Cons of VPNs
- Adversely affects performance – Since a VPN server introduces an additional hop to a connection, it can can cause delay. That delay gets worse if the user has to connect to an external site through the VPN server. The encryption and decryption process adds even more delay.
- Consumes mobile data faster – When a VPN encrypts data, it adds some overhead. Simply put, the transmitted data becomes larger. That additional overhead can cause mobile workers to use up mobile data faster than usual.
- Requires expert engagement – Most VPNs are difficult to deploy, configure, and maintain. Since a VPN can provide access to your entire network, you need to make sure sensitive systems aren’t unnecessarily exposed to external threats.
Now that you’re familiar with the advantages and disadvantages of firewalls and VPNs, let’s talk about when you would use each tool.
VPN vs Firewalls – When To Use One Over The Other
Let’s now go over some specific use cases that demonstrate when a VPN or a firewall should be used.
When should I use a VPN?
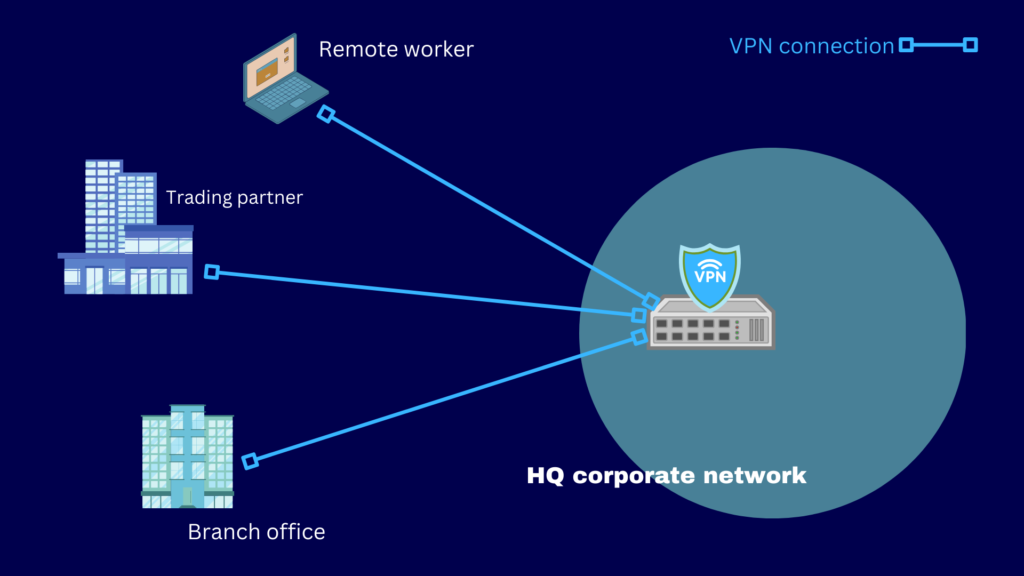
You would use a VPN in cases where you need a secure connection between your network and another endpoint or network. Here are some sample use cases that can benefit from a VPN:
- Remote workers attempting to access resources in your corporate network
- B2B data exchanges between you and your trading partners
- Data exchanges between your HQ and branch offices
In these three use cases, there will be times when it’s imperative to preserve confidentiality while data is being sent. The encryption capabilities of a VPN can help you achieve that objective.
When should I use a Firewall
You should use a firewall in cases where you need to apply a partial or complete restriction on network traffic. Here are some sample use cases that can benefit from a firewall.
- Partial restriction on inbound network traffic. For example, to prohibit insecure connections like FTP and HTTP.
- Partial restriction on outbound network traffic. For example, to prevent connections to unknown sites.
- Complete restriction between two network segments. For example, to prevent threats from moving laterally across your entire network.
In the use cases that require partial restrictions, you may, for example, set firewall rules that allow certain packets through but block everything else. In the use case that requires a complete restriction, you may configure the firewall to block all network traffic between segments.
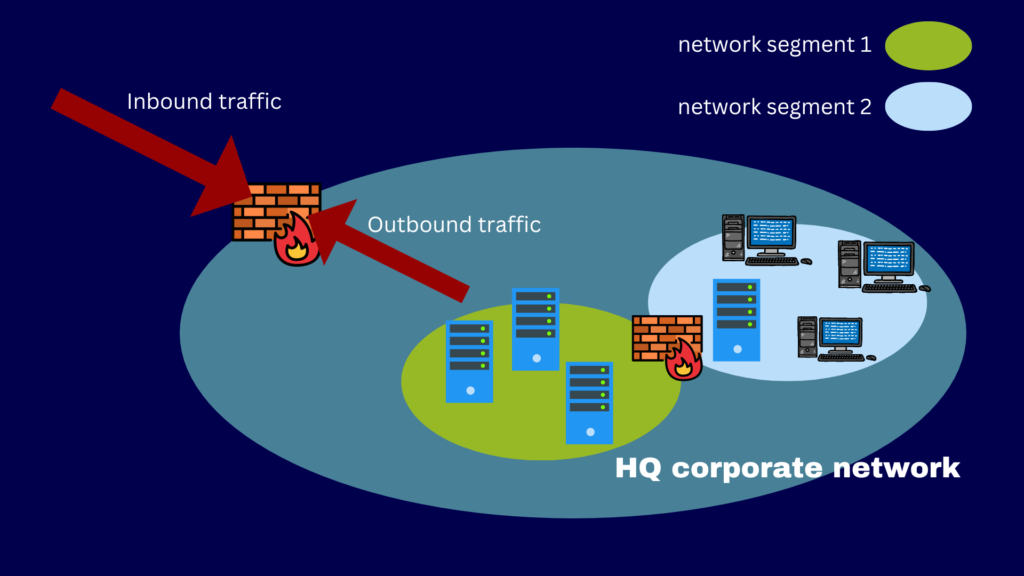
Should You Use Both Firewalls and VPNs together?
Both firewalls and VPNs play a crucial role in today’s highly connected, complex, and threat-infested business environments. Since VPNs and firewalls address different sets of threats and use cases, it makes sense to deploy them simultaneously.
A VPN can defend against any eavesdropping attempt to your inbound and outbound connections. Firewalls, on the other hand, can block undesirable inbound, outbound, and internal traffic.
The combination of a firewall and a VPN is inline with a defense-in-depth strategy. This strategy, which consists of multiple layers of security, is meant to address the existence of multiple threats.
We’re done here. Let’s sum everything up.
Final Words
In this VPN vs firewall article, you learned that firewalls and VPNs address different threats. Firewalls deal with inbound and outbound threats as well as threats that may move laterally inside your network. VPNs, on the other hand, deal with entities that threaten confidentiality when your data traverses the internet.
Since the threats that these two security solutions are all impending and completely distinct, those threats need to be dealt with accordingly. Instead of choosing one over the other, you might want to consider deploying both solutions in your network.
Did you encounter any questions in the course of your reading? Check out the FAQ and Resources sections below. You might find some answers there.
FAQ
What is a VPN service?
A VPN service is a VPN infrastructure managed by a third party service provider. Some VPN services are free, but the more advanced and more capable ones charge a monthly or annual fee.
What is a business VPN?
A business VPN is an encryption-driven technology that enables businesses to send data securely through a public network. When you employ a business VPN, you can conduct B2B data exchanges without worrying about threat actors eavesdropping on your connections.
What is a virtual firewall?
A virtual firewall is a firewall designed for virtual environments. You would use it primarily for securing virtual machines. Virtual firewalls possess similar security characteristics as physical firewalls but are generally cheaper.
How do you mitigate the risk of lateral movement in a data center?
There are several security controls you can apply in a data center that can help prevent lateral movement. You can deploy firewalls, IDS/IPS solutions, multi-factor authentication, and antimalware solutions, to mention a few. Our article on data center security has a more detailed discussion on the subject.
Can firewalls help secure IoT devices?
Yes, certain types of firewalls address security issues that involve IoT devices. In fact, some Next Generation Firewalls (NGFWs) have built-in features enabling IT admins to create firewall rules based on IoT traffic.