Intrusion Detection System (IDS) and Intrusion Prevention System (IPS) are two of the most widely used tools in modern cybersecurity environments. Now, you often see the terms IDS and IPS used in the same phrase, it’s almost as if they’re inseparable. Actually, they’re two different systems. My goal in this IDS vs IPS guide is to clearly define the similarities and differences of these two tools.
First, we’ll talk about IDS and IPS separately—what they are, how they work, the benefits they provide, and their different types. After that, we’ll put them side by side and make a clear and concise comparison so that when we’re done, you can easily distinguish one from the other.
That won’t be all though. You’ll also learn when you would use an IDS over an IPS, and vice versa. Lastly, you’re going to understand why, ideally, it’s best to deploy these two tools together. We’ve got a lot to cover, so let’s start the ball rolling. First, let’s clarify what we mean by an ‘intrusion’.
What is an Intrusion and How Does an IDS/IPS Detect One?
In the context of cybersecurity, an intrusion happens when an unauthorized entity manages to enter a certain system (e.g., a network or a host). That entity may be a threat actor deliberately infiltrating a system with harmful intentions. On the other hand, it may also be a non-malicious—but nevertheless unauthorized—entity that may have simply entered the system unintentionally.
IDS and IPS solutions can indirectly (as in the case of IDS) or directly (as in the case of IPS) prevent both undesirable cases from happening. Before any prevention can take place, the IDS or IPS must be able to detect the intrusion first. To do that, IDS and IPS solutions employ one or more of these intrusion detection methods:
Pattern or signature-based intrusion detection
Pattern or signature-based intrusion detection looks for patterns in network traffic or files and compares them with similar threat-related patterns in their database. This is similar to the way traditional antivirus software detect malware. Once a match is found—meaning, a potential threat is detected—the IDS/IPS generates an alert or blocks the threat.
Anomaly-based intrusion detection
This method usually employs machine learning (ML) technology to create a baseline that signifies safe or normal network traffic or files. Once the IDS/IPS detects a deviation from this normal behavior, that anomaly is interpreted as a potential threat and the IDS/IPS throws an alert or blocks it.
Policy-based detection method
In this method, the IDS/IPS compares traffic or files against a set of pre-configured security policies, much like a firewall. These policies are usually drawn up beforehand by someone from your IT/security team or built into the IDS/IPS by the IDS/IPS vendor. Once certain traffic is found to violate policy, an alert is generated or the IDS/IPS blocks the questionable packets.
Alright, now that we’ve put Intrusion Detection Methods 101 out of the way, let’s proceed with our discussion on IDS and IPS. Let’s talk about IDS first.
What is an Intrusion Detection System (IDS)?
An intrusion detection system or IDS is an appliance or software application that mainly detects an intrusion and then sends out alerts to log files, a SIEM, or some other security tool that ingests these types of data. The log data an IDS generates has to be interpreted by a trained threat analyst.
Note: A complete IDS deployment may actually be composed of multiple sensors (for a network-based IDS), agents (for host-based IDS), management servers, consoles, and databases. Most of these components are deployed separately. But for the sake of brevity, I’m just going to treat them as one entity—an IDS. That way, we can focus our discussion on the salient points that will help us make a clear IDS vs IPS comparison.
How Does an IDS Work?
An IDS works by monitoring inbound and/or outbound traffic and detecting intrusions through any of the detection methods we mentioned earlier. That is, by pattern or signature-based intrusion detection, anomaly-based intrusion detection, and/or policy-based intrusion detection. Once an intrusion is detected, a corresponding alert is sent.
Note that all the IDS does is detect an intrusion and, logs the event, and sends a corresponding alert. It doesn’t act on a threat even if it detects one. It’s up to the analyst to confirm the presence of a threat and act on it or ask someone else (e.g. an incident responder) to do so.
It might help you visualize how an IDS works if I showed you where it monitors traffic. Normally, an IDS (or more specifically, an IDS sensor) is deployed in this manner:
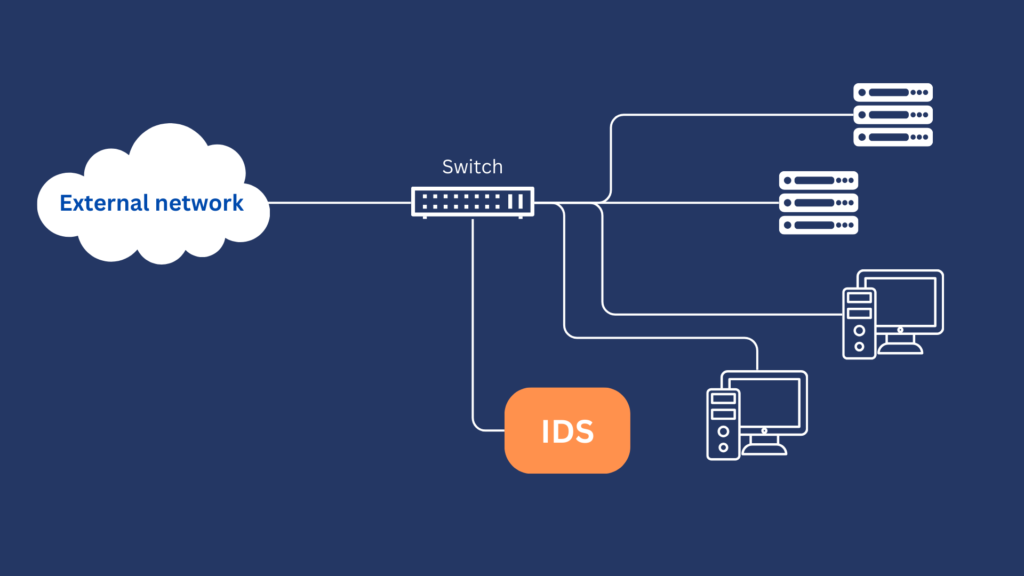
This is called an out-of-band or passive mode deployment and is usually implemented by connecting the IDS to a spanning port of a switch. A spanning port is a feature in certain switches that copies packets and redirects them to a target interface. In this case, the spanning port redirects those packets to an IDS.
Unlike an IPS, an IDS doesn’t have to be deployed inline (you’ll see how this looks later when we talk about IPS) because it just needs to inspect packets entering the internal network. It doesn’t have to block traffic itself when an intrusion is detected. Blocking requires that the blocking tool be deployed inline.
Note that the diagram above only applies to a network-based IDS (NIDS), which is arguably the most commonly used type of IDS. More about NIDS and other IDS types later. In the meantime, let’s discuss the benefits of using an IDS in general.
Benefits of an IDS
An IDS is capable of detecting a wide range of cyber threats. In addition, it will also alert your security staff, who can then take appropriate action. These attributes have substantial benefits. Here are some of them.
Provides more flexibility when countering a threat
While an automated response to potential threats (which is what you’ll get with an IPS) saves time, it can also cause unnecessary downtime if the detection turns out to be a false positive. An IDS won’t make an automated response. Instead, it’s going to alert your security analyst, who can then conduct further investigation and determine the most appropriate response. That response may amount to complete or partial downtime, or no downtime at all.
Detects DDoS attacks
Distributed Denial of Service (DDoS) attacks can crash servers and cause considerable downtime. By conducting network behavior analysis, an IDS can identify a DDoS attack and notify your security staff. Your security staff can then reconfigure your firewall to block packets involved in the attack.
Helps meet regulatory compliance requirements
Some data privacy/protection laws and regulations explicitly or implicitly recommend the use of IDS/IPS. PCI DSS, for example, requires the use of intrusion detection techniques to detect network intrusions. Needless to say, you can meet this requirement by deploying an IDS.
Detect network reconnaissance
Network reconnaissance is the act of running tests against a network to discover potential vulnerabilities. It usually precedes most hacking attempts, as it lets the hacker understand the “lay of the land”. You can employ an IDS as part of a layered defense to identify potential network reconnaissance activities and have a threat analyst investigate IDS log data indicating such activities. That way, you can catch a hacking attempt before it escalates.
As mentioned, the IDS we illustrated earlier was a network-based IDS or NIDS. There are other types of IDS as well. Let’s talk about those types now.
What are the Different Types of Intrusion Detection Systems (IDS)?
There are mainly four types of IDS—Network-based Intrusion Detection System (NIDS), Wireless Intrusion Detection System (WIDS), Host-based Intrusion Detection System (HIDS), and Network Behavior Analysis (NBA) with IDS functionality. It’s important to distinguish one from the other because they have certain nuances in how they’re deployed and what they inspect. Here’s a short comparison between the four types.
| IDS Type | Deployment | What it inspects |
| NIDS | NIDS sensors are deployed out-of-band a.k.a. passive mode (see diagram above) | Elements of network traffic, particularly packet header and payload/content. |
| WIDS | Depending on their design, WIDS sensors can be deployed using the following options: Fixed in strategic locations in your facilityInstalled on mobile devices (e.g., laptops, phones, or specialized mobile devices)Built into a wireless Access Point (AP)Built into a wireless switch | Wireless network traffic |
| HIDS | HIDS agents are installed on endpoint devices or hosts, such as PCs or servers | Application-generated log files, changes to the registry, system processes. |
| NBA/IDS | NBA/IDS sensors are deployed inline | Sometimes network packets, but usuallynetwork flow information generated by routers and other network devices |
Alright, that’s all I wanted to cover about IDS. Let’s now move on to IPS.
What is an Intrusion Prevention System (IPS)?
Like an IDS, an Intrusion Prevention System or IPS also detects potential threats and sends alerts. However, unlike an IDS that only detects an intrusion while it’s underway, an IPS can actually prevent the intrusion from taking place. An IPS automatically blocks threats before they can enter the network or host behind that IPS. Let me elaborate more on this by explaining how an IPS works.
Note: A complete IPS deployment may actually be composed of multiple sensors (for a network-based IPS), agents (for a host-based IPS), management servers, consoles, and databases. Most of these components are deployed separately. But for the sake of brevity, I’m just going to treat them as one entity—an IPS. That way, we can focus our discussion on the salient points that will help us make a clear IDS vs IPS comparison.
How Does an IPS work
Just like an IDS, an IPS monitors network traffic and then uses intrusion detection methods (review discussion above) to detect potential threats. However, unlike an IDS, an IPS doesn’t stop at detection. It also automatically blocks perceived threats upon detection.
In order for an IPS to do this, you would normally deploy it inline as shown below. Notice that the IPS is facing the external network. An IPS has to be deployed in this manner because it has to be in the path of incoming traffic in order to block threats it detects. Any packet that’s tagged a threat by any of the intrusion detection methods is automatically blocked. Unlike in an IDS, this action doesn’t require any human intervention.
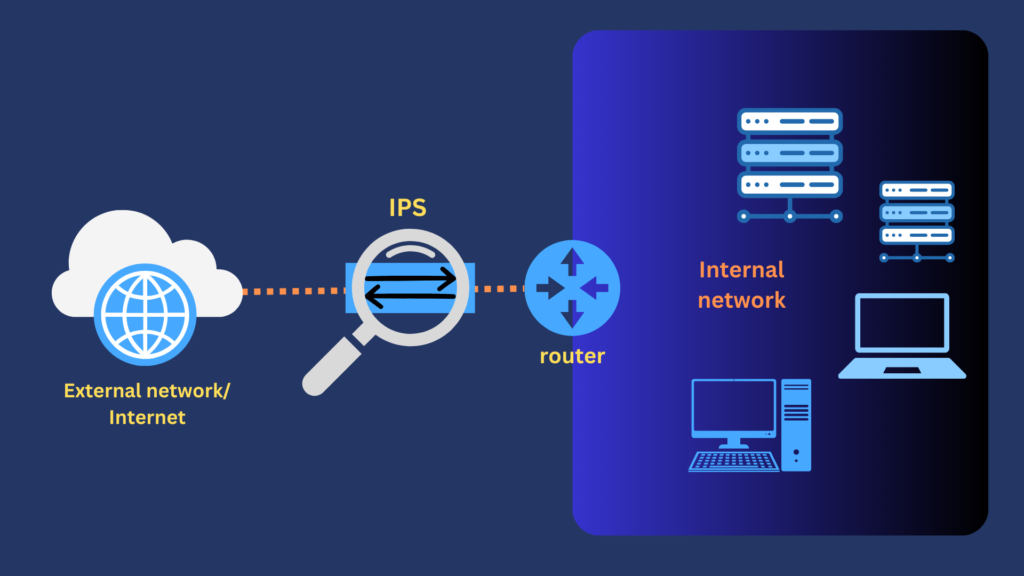
Notice that the malicious packets are blocked before they can reach the internal network behind the IPS. Hence, technically speaking—and assuming the IPS is configured perfectly—no intrusion would have taken place. Yes, the threat may have already intruded into the zone where the IPS is located, but not the zone behind it. Hence the term ‘intrusion prevention’.
In a way, this auto-blocking feature gives an IPS a significant advantage over an IDS. Note that the diagram above only applies to a network-based IPS (NIPS), which is arguably the most commonly used type of IPS. More about NIPS and other IPS types later. In the meantime, let’s discuss the benefits of using an IPS in general.
Benefits of an IPS
Most of the benefits you’ll get with an IDS can also be acquired through an IPS. The ability to detect DDoS attacks and network reconnaissance as well as achieve regulatory compliance, for instance, can also be had with an IPS. However, because an IPS automatically prevents an intrusion, it comes with a few additional benefits.
Automatically blocks threats
If you recall, an IDS only alerts you of an intrusion. It can’t prevent that intrusion from taking place. In some cases, detection and alerting won’t be enough. What if the person analyzing the IDS logs somehow fails to make the right assessment and response? In cases like this, some threats can slip through. With an IPS, you’ll be less susceptible to intrusions because it’s going to automatically block a perceived threat upon detection.
Reduces security staffing requirements
An IDS can’t be effective if you don’t have security staff who can analyze IDS logs, identify potential threats from the logs, and perform incident response. Because an IPS can act on its own, detecting and blocking potential threats automatically, you’re staffing requirements won’t be as steep.
Frees up your security team
Even assuming you have a dedicated security team, an IPS can free team members from threat analysis and incident response tasks since it can do a lot of those tasks on its own. This means your security team can simply review IPS activity and focus more on other risk mitigation efforts.
As with IDS tools, there are also different types of intrusion prevention systems.
What are the Different Types of Intrusion Prevention Systems (IPS)?
Like IPS, there are mainly four types of IDS—Network-based Intrusion Prevention System (NIPS), Wireless Intrusion Prevention System (WIPS), Host-based Intrusion Prevention System (HIPS), and Network Behavior Analysis (NBA) with IPS functionality. It’s important to distinguish one from the other because they have certain nuances in how they’re deployed and what they inspect. Here’s a brief comparison between the four types.
| IPS Type | Deployment | What it inspects |
| NIPS | NIPS sensors are deployed inline (see diagram above) | Elements of (wired) network traffic, particularly packet header and payload/content. |
| WIPS | Depending on their design, WIPS sensors can be deployed through the following options: Placed in strategic locations in your facility (these are for dedicated appliances)Installed on mobile devices (e.g., laptops, phones, or specialized mobile devices)Built into a wireless Access Point (AP)Built into a wireless switch | Wireless network traffic |
| HIPS | HIPS agents are installed on endpoint devices or hosts, such as PCs or servers | Application-generated log files, changes to the registry, system processes. |
| NBA/IPS | NBA/IPS sensors are deployed inline | Sometimes network packets, but usuallynetwork flow information generated by routers and other network devices |
Ok. We’re finally ready for the main course of this article. It’s time to discuss the similarities and differences between IDS and IPS.
IDS vs IPS – Similarities and differences
We already discussed the main qualities of an IPS and an IDS earlier in this article. Let’s now compare and contrast the two based on the information we know.
Similarities of IDS & IPS
IDS and IPS tools are almost similar to one another. For one, both tools employ the same intrusion detection methods, namely:
- Pattern or signature-based intrusion detection
- Anomaly-based intrusion detection
- Policy-based intrusion detection
If you’ve noticed, most IDS and IPS types also have similarities in the manner they’re deployed and what they inspect. For example, both HIDS and HIPS agents are installed on endpoint devices and both WIDS and WIPS inspect wireless network traffic.
Both IDS and IPS systems can also send out alerts. However, while an IDS only sends out alerts, an IPS also takes action without any human intervention. That’s not the only difference between IDS and IPS.
Key Differences Between IDS & IPS
Again, we already discussed the main qualities of an IPS and an IDS earlier. So, as with the similarities above, I’m just going to present the differences in summary form. I’m putting them side by side so you can clearly see the key differences.
Note that, for the differences in deployment, this only applies to network-based types of IDS and IPS, i.e., NIDS and NIPS. However, it’s important to point these out because network-based IDS and IPS are the most widely used types.
| Key Differences – IDS vs IPS | ||
| IDS | IPS | |
| Main Functions | Detects intrusions and sends alerts | Detects potential intrusions and blocks them. Optionally sends alerts |
| Deployment | Normally passive / out-of-band via a spanning port or network tap | Normally inline |
| Autonomous | No. Normally needs to send alerts to threat analysts | Yes |
In case it still isn’t clear, an IDS detects intrusions, while an IPS blocks them. This behavior has a lot to do not only with how they’re designed to operate, but also how they’re deployed (out-of-band vs inline). Lastly, an IDS can only help in preventing threats if you have security staff manning them, whereas an IPS can act autonomously.
Now that you know the similarities and differences of an IDS and an IPS, it’s time to discuss when you would normally use one over the other.
Should I use IDS, IPS, or both?
Since an IPS can act autonomously, it might seem to be the more advanced security tool and the better choice. Not necessarily. One disadvantage of an IPS is that in the event of a false positive (e.g. the IPS wrongly tags legitimate traffic as a threat), the IPS can unintentionally block a completely legitimate business process.
An IDS is less susceptible to these types of blunders because, in the event that suspicious traffic is detected, the IDS still has to send alerts to a security analyst. The (presumably highly trained/experienced) security analyst can still analyze the traffic in question and confirm if it is in fact a threat or not. Of course, this process requires that you have a security analyst in the first place.
When to use an IDS
Thus, generally speaking, if you have security analysts (whether in-house or third party-affiliated) who can analyze alerts and act on them, an IDS might be more suited for you. You’ll also want to use an IDS if the system you want to protect with it is too crucial to be taken offline (e.g. critical infrastructure) by a mere a false positive.
When to use an IPS
On the other hand, if you don’t have security analysts and want something that acts autonomously, an IPS would be the better choice. You’ll also want to use an IPS if the system you want to protect with it really can’t afford any threat to get through. For example, a database with lots of personal data. In this case, the prospect of a data breach can be more damaging than a false positive that would take the system offline.
When to use both
All that being said, ideally, you would want to deploy an IPS and an IDS together. Here’s one sample scenario that illustrates the benefit of pairing an IPS with an IDS. In this scenario, you have an IPS in front of a router facing an external network, say the internet. Behind that router is a switch connecting to your internal network and an IDS connected to that switch’s spanning port.
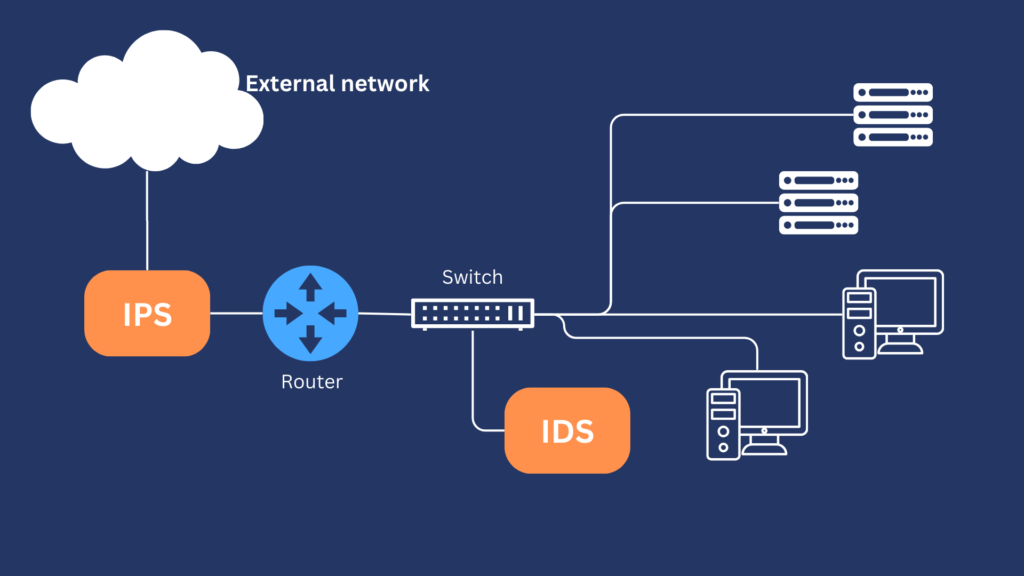
Now imagine you’ve configured the IPS with relatively lenient filtering rules and the IDS with relatively stringent filtering rules. This would allow the IPS to filter out only clearly defined unwanted traffic and allow all other traffic, especially legitimate traffic, to pass through.
On the other hand, it would allow the IDS to detect and alert you of ALL suspicious traffic. That would include both true positives and false positives. That’s ok because your security analysts can still analyze those alerts and identify any false positives. You can then fine-tune your IDS and IPS accordingly until you reach your ideal configuration.
IDS/IPS tools are often used, deployed, or managed by the following cybersecurity professionals:
- Cloud security analysts
- SOC analysts
- Network security engineers
- Incident responders
- Threat hunters
- Penetration testers
- Cybersecurity architects
The Bottom Line
The main goal of this IDS vs IPS article was to articulate clearly and concisely the similarities and differences between IDS and IPS. By now, you should know that both IDS and IPS employ similar intrusion detection methods. You should also know that, aside from NIDS and NIPS, the different types of IDS and IPS have similarities in the manner they’re deployed and what they inspect.
As with regards to the differences between IDS and IPS, there are three key points to remember:
- IDS detects intrusions and sends out alerts, whereas IPS detects potential intrusions and prevents them from happening;
- The difference in IDS and IPS deployments is most distinguishable in their network-based types, i.e., NIDS and NIPS. NIDS sensors are normally deployed in passive mode, while NIPS sensors are normally deployed inline.
- An IDS requires security staff to act on its detections, whereas an IPS can act autonomously.
I hope you’ve reached this far with a clear understanding of the similarities and differences of IDS and IPS. In case some questions bubbled up during the course of our discussion, you can check the FAQ and Resources sections below. It’s possible that some of those questions have been answered there.
FAQ
What is a DDoS attack?
A Distributed Denial of Service or DDoS attack is a network-based attack built to overwhelm the target’s computing resources. These attacks can disrupt your network’s performance and prevent legitimate users from connecting. Certain types of IDS and IPS can directly or indirectly thwart a DDoS attack.
What is incident response?
Incident response is the process of addressing a perceived threat. Incident response is usually carried out by trained security staff. It usually comes into play after a threat has been detected by tools such as an IDS or an IPS.
What is a network tap?
A network tap is another way of connecting an IDS out of band. It’s a direct connection between the IDS and and the physical network itself, e.g., fiber optic cable. As with a spanning ports, a network tap will allow you to view a copy of the network traffic transmitted over the media being tapped.
What is network flow?
Traffic flow, packet flow, or network flow refers to a set of packets passing through a point in the network over a particular time interval. Certain flow data, such as source/destination IP addresses, number of packets and bytes transmitted in a session, etc., provide insights for intrusion detection and prevention. Flow data is typically collected through protocols like NetFlow and sFlow.
What is Machine Learning?
Machine Learning (ML) is a field in computer science that focuses on using data and algorithms to mimic how humans learn. ML-based techniques are used alongside other detection methods in modern intrusion detection and prevention systems.