So you’ve just set up your network and are now ready to add some security to it. The first thing that comes to mind is… surprise, surprise… a firewall. Good call. But what type of firewall? As of this writing, I’d say there are 8 major types of firewalls to choose from.
Each of these firewall types have their own advantages and disadvantages. One firewall might be better suited for a particular use case than another. Also, different firewalls operate on different layers in the Open Systems Interconnection (OSI) or Transmission Control Protocol/Internet Protocol (TCP IP) conceptual model.
Before I go over each of those 8 types of firewalls, allow me to give a brief overview on what a firewall is and how these network security tools work.
What is a Firewall?
A key component of business IT networks, the firewall is a network security tool that filters inbound and outbound traffic based on a set of rules or conditions. In the past, firewalls were normally positioned at network perimeters to protect an organization’s internal network from external threats.
Today, however, firewalls are now also increasingly being used in other areas in the network to provide additional layers of security or to help implement network segmentation. So, for example, you can use a firewall to restrict access to your financial or human resource systems from other parts of your organization.
With these capabilities, firewalls can help you keep undesirable traffic out of your networks as well as prevent unauthorized outbound connections from getting established. So how do they do that? Well, it depends on the type of firewall, although they do have some similarities in the way they work.
How do Firewalls work?
Generally speaking, firewalls work by allowing or denying network traffic based on certain rules or conditions. Depending on the type of firewall, these rules or conditions operate on specific layers of the TCP/IP or OSI conceptual model. For example, packet-filtering firewalls usually operate in the network layer of the OSI model, while application firewalls are capable of operating in the application layer.
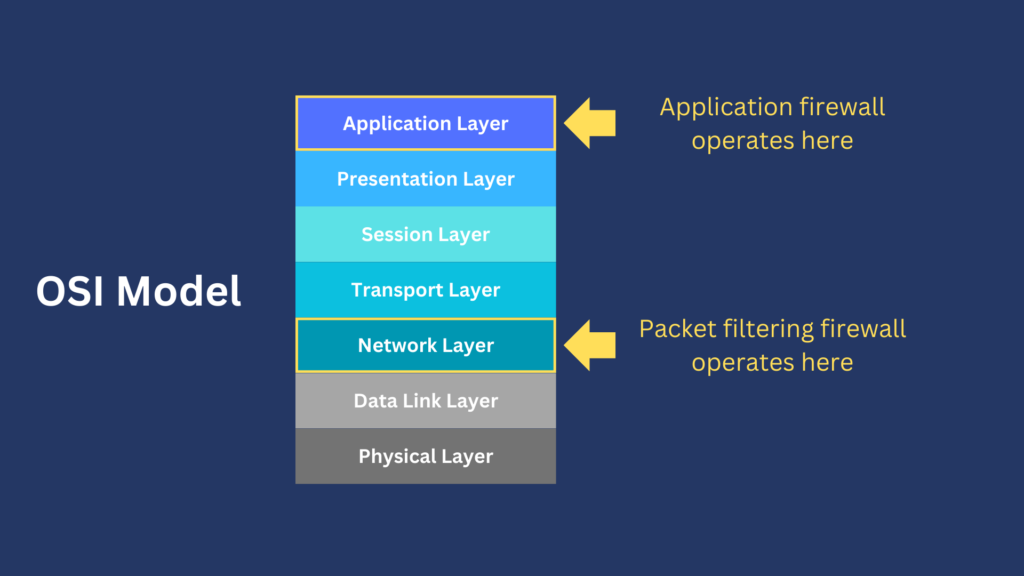
Basic firewalls are only capable of inspecting one or two layers and usually only focus on the lower layers, e.g., the network and transport layers. As you’ll see later in this article, the more advanced a firewall is, the more layers it is able to inspect and filter. If you’re looking for a firewall that can perform more granular inspections, you’ll want to search among the advanced firewall types. I’ll show you what they are in the next section.
8 Types of Firewalls
1. Packet-Filtering Firewalls
This is the most basic type of firewall. It filters out traffic based on a set of rules—a.k.a. the firewall’s ‘ruleset’—that apply to the network layer and, in some cases, the transport layer. It only inspects a packet’s header.
So, for example, you can specify a packet-filtering firewall rule that restricts inbound traffic to packets coming from a specific IP address or a range of IP addresses. You may also for example, add a rule that only allows certain transport layer protocol traffic, say TCP, to pass through.
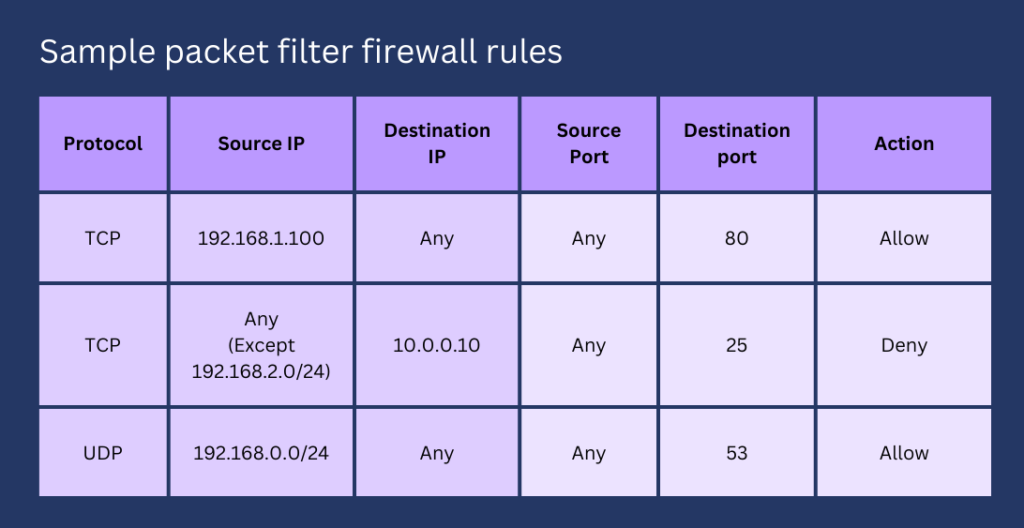
Due to its simplicity (compared to other types of firewalls) and the degree of inspection it performs, packet filtering firewalls have the following advantages compared to other firewalls.
Advantages
- Faster
- More affordable
- Less impact on network performance
However, also because of its simplicity, it has the following disadvantages:
Disadvantages
- Doesn’t inspect the packet’s payload. So, if that payload is malicious, but its packet header values satisfy your ruleset, it will be allowed to pass.
- Most of them are stateless, i.e., they lack awareness of the state of a connection. Hence, they can’t determine beyond valid packet header values if a connection is truly authorized. This makes them vulnerable to spoofing attacks.
- Their access control lists (ACLs) can be very tedious to set up and maintain.
While this type of firewall can certainly provide a decent level of protection, it’s not as effective against sophisticated threats as other, more advanced, types of firewalls, Hence, you would typically use a packet-filtering firewall for networks with moderately valuable assets or as your first line of defense in a multi-layered defense strategy.
2. Circuit-Level Gateways
Another basic type of firewall is the circuit-level gateway firewall. This firewall mainly operates in the session layer, the layer that deals with TCP handshakes and other mechanisms related to connection establishment, management, and termination. It inspects the messages involved in these mechanisms and compares it with predefined session rules to determine whether a session is legitimate or not, and then blocks if it finds the session suspicious.
Let’s say for example a session rule defines a valid session as one that’s initiated by a recognized device. If a session is initiated by an unknown device, that session is automatically blocked. Because of their simple architecture and function, circuit-level gateways have more or less the same advantages and disadvantages as packet-filtering firewalls compared to other, more advanced firewalls.
Advantages
- Faster
- More affordable
- Less impact on network performance
Disadvantages
- Completely unaware of any threats lurking in a packet’s payload.
- Only operates on a single layer—the session layer
You would normally deploy a circuit-level gateway firewall in cases where you have a limited budget (or simply don’t need a highly advanced firewall) but want something that’s at least slightly better than a packet-filtering firewall.
3. Stateful Inspection Firewalls
Like packet-filtering firewalls, a stateful inspection firewall also operates in the network and transport layers. It also inspects packets and then checks to see whether they satisfy the firewall’s ruleset. If they do, they are allowed to pass through. However, it doesn’t stop there. In addition, the firewall also records certain information about each packet into what is known as a ‘state table’ and then keeps track of those values to determine whether a packet being inspected aligns with its expected state. If it doesn’t, it is blocked.
A packet-filtering firewall can, for instance, determine whether an inbound packet is part of a currently open connection. If it is, and since that connection is assumed to have already been authorized, that packet can be automatically deemed safe.
Advantages
- Has better context than packet-filtering firewalls when determining what to block.
- It can dynamically open and close ports based on the state of a connection, thereby reducing exposure to potential threats such as port scanners.
- Generates detailed logs that can help in digital forensics.
Disadvantages
- More resource intensive than packet-filtering firewalls
- More expensive than packet-filtering firewalls
- Susceptible to TCP flood attacks or other DDoS attacks that exploit ‘stateful’ characteristics
You would normally employ this kind of firewall for use cases that require something that does more than just simple packet filtering but isn’t as expensive as a proxy firewall (see below).
4. Proxy Firewalls (aka application-level gateway)
Proxy firewalls operate in the highest layer of both the OSI and TCP/IP models—the application layer. They’re capable of inspecting the actual content of a packet, not just the headers. This is known as deep packet inspection or DPI. But what really sets proxy firewalls apart is their ability to prevent two communicating hosts/devices from connecting directly with one another while making it appear to each device that they are (establishing a direct connection).
When two hosts/devices connect through a proxy firewall, two connections are actually established. One between the first host/device and the firewall, and another between the firewall and the second host/device. This means that if external clients connect to servers behind your proxy firewall, those external clients won’t ‘see’ the IP address of those servers. In effect, a proxy firewall can conceal internal IP addresses from external clients.
Advantages
- Provides a kind of security (concealing internal IP addresses and ports) that can complement what most types of firewalls provide.
- Examines not only packet header information, but also packet content.
- The ability to conceal internal IP addresses prevents threat actors from gathering valuable intelligence about your internal network.
Disadvantages
- Can increase latency since it’s more thorough when inspecting a packet.
- More expensive than even stateful inspection firewalls.
- Supports a limited number of network protocols
The ability to conceal internal IP addresses is very useful from a security standpoint, as it adds a completely different element to firewall security. However, because proxy firewalls can’t support certain network protocols, I would recommend you employ another type of firewall—perhaps a packet-filtering or stateful inspection firewall—to complement it.
5. Next-Generation Firewalls
Sitting at the top of the firewall hierarchy in terms of features (and price) are the Next Generation Firewalls (NGFWs). These firewalls combine all the capabilities of packet filtering and stateful inspection firewalls with additional features such as DPI, intrusion detection system/intrusion prevention system (IDS/IPS), and malware protection, among others.
In the context of an NGFW, IDS/IPS are features that analyze packet information and behavior through various threat detection techniques such as pattern matching, protocol-based detections, heuristic-based detections, and anomaly-based detections. We won’t go into the details, but these are various techniques that help detect the presence of potential threats.
By combining DPI (that allows the firewall to conduct a more thorough inspection), IDS/IPS, and malware protection (which allows the firewall to act on a malware threat when found), an NGFW can act on a wider range of threats than other types of firewalls.
Advantages
- Provides multiple security capabilities in one solution.
- Inspects almost all layers (from the data link layer all the way up to the application layer).
- Capable of decrypting SSL/TLS-encrypted traffic to inspect the content.
Disadvantages
- Very expensive. Might be impractical for most small businesses.
- DPI, IDS/IPS, and malware protection, require more system resources.
Because of their extensive capabilities and their price tags, you would normally purchase a NGFW if you’re going to use it in a large organization or enterprise. The level of security an enterprise normally requires makes it worth purchasing a NGFW. For many small businesses, it might be overkill.
Most of our classifications of firewall types have so far been based on how these firewalls operate and the TCP/IP or OSI layers they operate on. You can also classify firewalls based on their delivery methods, i.e., whether they are software–based, hardware-based, or cloud-based. Let’s talk about those in the succeeding sections.
6. Software Firewalls
Software firewalls a.k.a. host firewalls are basically software applications and, hence, are installed on the devices they are meant to protect. Just like regular applications, this type of firewall takes up CPU, RAM, and storage resources of the devices they’re installed on.
Since these firewalls operate on a specific device, they have better awareness of the applications and processes that run on that same device. This allows them to provide more granular security on that particular device.
Advantages
- Can provide highly targeted restrictions, such as allowing access to one application while denying access to another.
- They’re readily available. Major operating systems such as Windows, macOS, and Linux already have software firewalls built-in by default. You may of course install third party alternatives if you want.
Disadvantages
- Competes with other applications for CPU, RAM, and storage resources on the devices they are installed on
- Third party software firewalls may not support certain platforms. For example, if a particular software firewall only provides installers for Windows, you can’t use it to secure your Mac and Linux devices
- Third party software can be difficult to deploy and administer, since they have to be installed on each individual device.
You may deploy software firewalls on mission-critical hosts to bolster that host’s defenses.
7. Hardware Firewalls
Hardware firewalls a.k.a. appliance firewalls are network devices with firewall capabilities. Being a separate device, it takes up its own CPU, RAM, and storage resources. Hardware firewalls are normally positioned at a network’s perimeter, acting as a gatekeeper between the external network and the internal network.
In most cases, that external network will be the Internet, and the internal network will be your own network. However, you can also position the firewall between two internal networks that need to be separated from each other.
Advantages
- Since they’re generally fewer than software firewalls (which run on each individual device), they’re easier to manage if you have someone trained to manage them.
- Doesn’t compete with the applications on your servers and other endpoint devices for compute resources. It consumes its own.
- A single hardware firewall can protect an entire network, whereas software firewalls can only protect the device it is installed on.
Disadvantages
- Requires administrators who are trained for it
- More expensive than software firewalls
Because a single hardware firewall can already secure multiple hosts and endpoint devices running in the same network, you should consider deploying one at your network perimeter.
8. Cloud Firewalls
A cloud firewall or Firewall-as-a-Service (FaaS) refers to any cloud-based service that acts as a firewall—usually a proxy firewall. As with other cloud solutions, cloud firewalls are managed and operated by third party cloud solutions providers. Almost all administrative tasks, including installation, deployment, patching, and troubleshooting are handled by the FaaS provider.
Advantages
- Frees your IT admins from firewall-related administrative responsibilities
- Scalable (just like all cloud solutions)
- Zero upfront costs
- Flexible pricing. Again, just like other cloud solutions, FaaS can be had through subscription or consumption-based pricing.
Disadvantages
- Your traffic goes through a third party. For some businesses, that’s not very appealing from a privacy standpoint.
- The recurring costs of cloud-based firewalls can be more expensive than the upfront cost + operational costs of a non-cloud firewall in the long run.
As with other cloud solutions, you would typically go for a cloud firewall if you have no qualms about routing your network traffic through a third party and would prefer spending more in the long run than paying a huge upfront cost.
Which firewall is best for your business?
Every organization is unique in that the assets you need to secure, the resources you have to secure them, your risk appetite, your network layout, and so on, will differ from that of another organization. Hence, the firewall or firewalls ideal for your business will be unique to your specific needs. Here are some of factors to consider:
Level of security required
What do you have behind your firewall? Do you have thousands of personal information? Are your trade secrets stored there? How about financial or customer data? Are you running a business-critical server behind it? If you can’t afford to have any of the hosts or endpoint devices behind that firewall compromised, you should be willing to deploy one of the advanced types of firewalls. But if not, then perhaps a simple packet-filtering or circuit-level gateway firewall will suffice.
Budgetary constraints
Not everyone has an unlimited budget. If your organization needs to protect sensitive data but simply can’t afford a next generation firewall, then you’ll probably have to go for more affordable options. A stateful inspection firewall or even a packet filtering firewall is better than no firewall at all.
Risk appetite
Before you get the cheapest option, you need to consider how much risk you’re willing to take or how much risk you can afford to take. If you’re dealing with any type of data that’s covered by data privacy/protection laws and regulations, you need to take into consideration the potential costs if you suffer a data breach.
Size of your network
The size of your network can also help determine the types of firewalls you should include in your shortlist. If you have a massive network, maybe a software-based third party firewall might be too impractical. It would probably be better from an administrative and cost-efficient perspective to purchase a hardware-based firewall for this purpose.
Possible combinations
Ideally, however, because different firewalls have different strengths, you might also want to consider employing multiple firewalls and apply a defense-in-depth (or multi-layered) approach to network security. Basic firewalls such as packet filtering firewalls can be used in tandem with more advanced firewalls such as stateful inspection firewalls or proxy firewalls.
The Bottom Line / Final Words
There are different types of firewalls. Each one is best suited for a particular purpose or use case. You have firewalls for limited budgets, firewalls for business-critical networks, firewalls for large business or small businesses, and so on. Before you can pick the right firewall, you need to know what each firewall type is built for. We took care of that earlier.
In this post, you learned 8 different types of firewalls, their advantages and disadvantages, and how to choose between these types of firewalls for your business. I mentioned a few terms that might have sounded new to you. See if you can find them in the FAQ section below. I’ve also added a few relevant resources in case you want to read some more.
FAQ
What is a spoofing attack?
A spoofing attack is an attack wherein a malicious entity is made to impersonate another—usually trusted—entity using information associated with that second (trusted) entity. For example, in an IP spoofing attack, threat actors modify IP packet source addresses to make it appear they are coming from a different source.
What is an Access Control List (ACL)?
A firewall ACL or ruleset is a list of allow/deny conditions or rules. It’s where the firewall looks up rules to determine whether a packet should be allowed or denied access. Depending on the hosts, services, and applications that are behind that firewall, these lists can be quite long—like, hundreds of thousands of lines long.
What is a DDoS attack?
A Distributed Denial of Service attack is a type of cyber attack that indundates a network or network device (such as a firewall) and prevents it from receiving connections. In other words, it denies users access to whatever service the network or device normally provides.
What is a TCP flood attack and how does it exploit a stateful firewall?
In the context of a stateful firewall, a TCP flood attack is a DDoS attack that floods a stateful firewall with SYN packets until it can no longer receive additional inbound connections.
Basically, SYN packets are normally sent by a client that’s attempting to establish a TCP connection. In turn, the device records these requests in a state table and then responds with a SYN-ACK message. Since the client in this case is actually malicious, it doesn’t respond with the expected ACK message.
This forces the device to keep the TCP connection and the state entry in the table open as the firewall keeps track of the connection’s state. This consumes memory. As more SYN packets come in, more memory is consumed until the device ceases to accept more requests—including legitimate ones.
What is digital forensics?
Digital forensics is the science of identifying, processing, and analyzing electronic data, usually with the intention to find evidence of cybercriminal activities and to understand how such activities were carried out.