When you’re still learning about VPNs, whether for educational or buying purposes, it’s important to bear in mind that there are different types of VPNs. Some types of VPNs are already obsolete or at least no longer suited for business environments for security reasons. There’s still a ton of material on the web about those obsoleted types, but you probably want to focus on the more current VPNs.
Some VPN types are also more suited for a particular use case than others. If you want to be sure you’ll be using the right type for your business, you need to be familiar with the different types of VPNs. In this article, we’re going to have a comprehensive look at the various types of VPNs. Since VPNs are usually classified by architecture and by protocol, we’ll break them down through the lens of these two classifications.
Before we do that though, let’s first review what a VPN is.
What is a VPN? A Brief Review
A virtual private network or VPN enables you to extend your private network across a public network like the Internet. At the same time, it keeps your connections safe from eavesdroppers. By using a robust VPN, authorized users can send and retrieve files, messages, and other data with no risk of them being intercepted and stolen or tampered. In other words, a VPN upholds data confidentiality and integrity.
VPNs are currently in demand with the rising adoption of remote and hybrid work. A recent report indicated that the global VPN market is expected to grow at a CAGR of 20% from 2023 to 2032.
How Do VPNs work?
Continuing our discussion above, let’s dive a bit into how VPNs work. Imagine your own private, company network. Your firewall isolates everything in that network from the outside world. Your internal users can securely access files, servers, printers, etc, in that network. That’s well and good, but what if you want remote users to access those same IT assets too?
Your remote users would have to access those internal assets through the Internet, a public network teeming with various threats. To retrieve network packets from your internal network through the Internet, those remote users can employ a technology that uses tunneling. Tunneling encapsulates packets intended for a private network so they can traverse a public network. VPN is one technology that uses tunneling.
In addition, a VPN secures your remote users’ connections through encryption, which renders data unreadable. Meaning, even if threat actors can intercept your users’ connections, they won’t be able to retrieve any useful information. Any intercepted data will just appear gibberish.
By using a business VPN, your remote workers can securely access your internal servers, files, and even printers. It’s going to be as if they were inside your company network. That’s what we mean by saying, “a VPN extends your private network”.
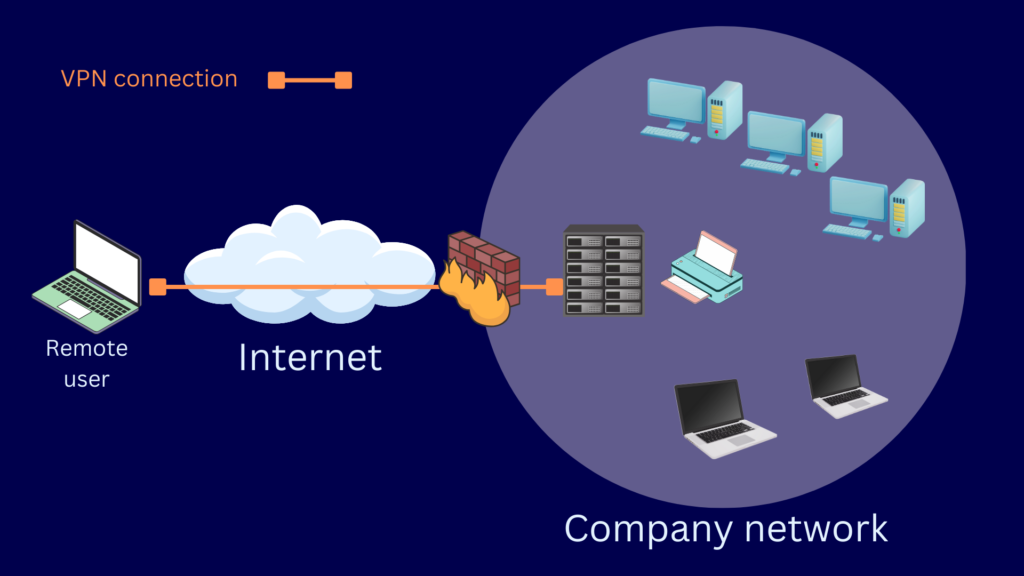
The scenario we just described depicts a specific VPN architecture known as remote access. There are other VPN architectures too. Let’s talk about the three main types of VPN architectures now.
Types of VPNs, Based on Architecture
A VPN architecture refers to the way a VPN environment is structured. The four (4) main VPN architectures include remote access, site-to-site, host-to-host, and consumer VPNs. Let’s talk about these four architectures in more detail.
Remote Access VPN
Remote access refers to the VPN architecture that consists of external users and an internal network behind a VPN gateway or server. In this architecture, external users need a VPN client to connect to the VPN gateway on the network or ‘site’. For this reason, remote access VPN is also known as client-to-site VPN or client-based VPN. The client is normally a piece of software installed on the user’s device.
Remote access VPN is ideal for situations where you have remote users who need access to your internal network. Users can securely connect to your network regardless whether they’re at home, in a hotel, in an airport, or just about anywhere. Scroll back up to see what a typical remote access VPN looks like.
Site to Site VPN
Site-to-site VPN or gateway-to-gateway VPN is a VPN architecture that connects two separate networks. To implement this architecture, you would need a VPN gateway or server on each network. Unlike remote access, this architecture doesn’t require you to install any client software. Once the two VPN gateways are connected, users that reside in both networks can access resources in the other network.
You’ll want to use a site-to-site VPN if you want to connect a branch office with your HQ network. You can also use these types of VPNs to connect a trading partner’s network with your network.
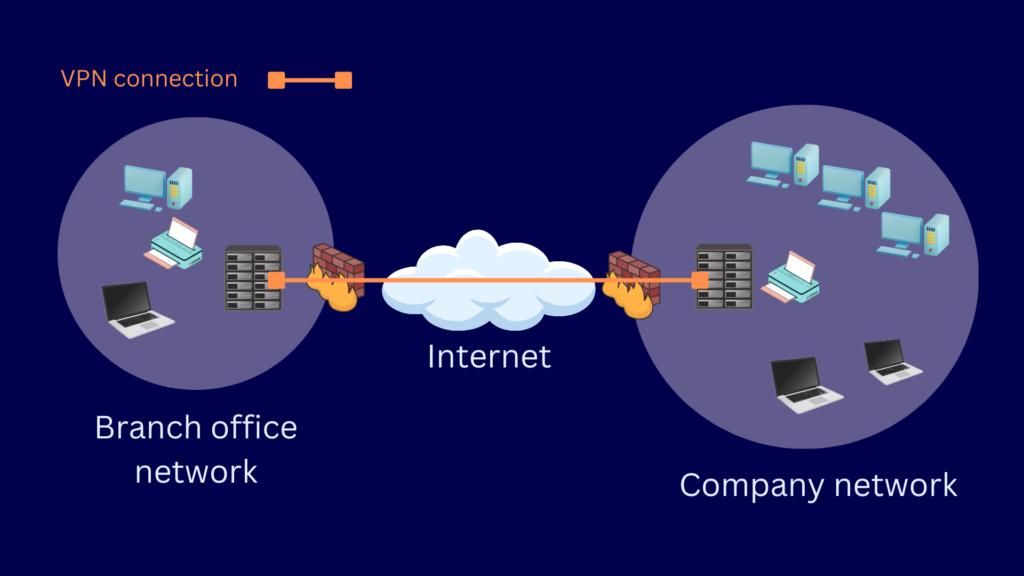
Host to Host VPN
A host-to-host VPN is similar to remote access VPN. This VPN architecture also requires a VPN client on one end. The main difference is that instead of using a VPN gateway, the other endpoint provides the VPN service itself. That “other endpoint” is usually a server with a VPN service running on it.
You normally use these types of VPNs if your system administrators need secure access to a highly sensitive server. You can lock down that server and limit access through a host-to-host VPN. Only authorized users who have VPN clients configured for that server’s VPN service can access that server. In the diagram below, the system administrator’s laptop acts as one host and the server on the other end acts as another host.
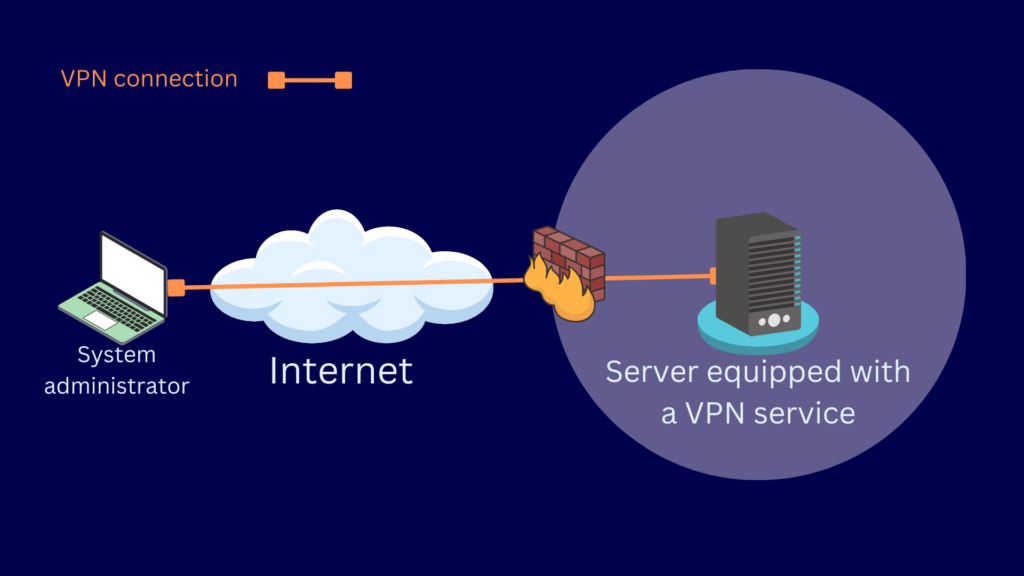
Consumer VPN
Also known as commercial VPN services, consumer VPNs are VPNs delivered as a service by third-party providers like ExpressVPN, NordVPN, and Surfshark. This type of VPN requires users to install VPN clients on their endpoint devices such as laptops, PCs, phones, and tablets. Although consumer VPNs can also encrypt your data, most consumers use these types of VPNs to acquire anonymity while using the internet.
When you use a consumer VPN, sites you visit won’t be able to see your real IP address. Instead, they’ll see an IP address associated with a VPN server owned by your VPN service provider. These providers own a large selection of VPN servers around the globe. So, for example, if you’re in China and you connect to a VPN server in the US, you’ll acquire a US IP address. When you visit a website, that site will see that US IP address instead of your real IP address.
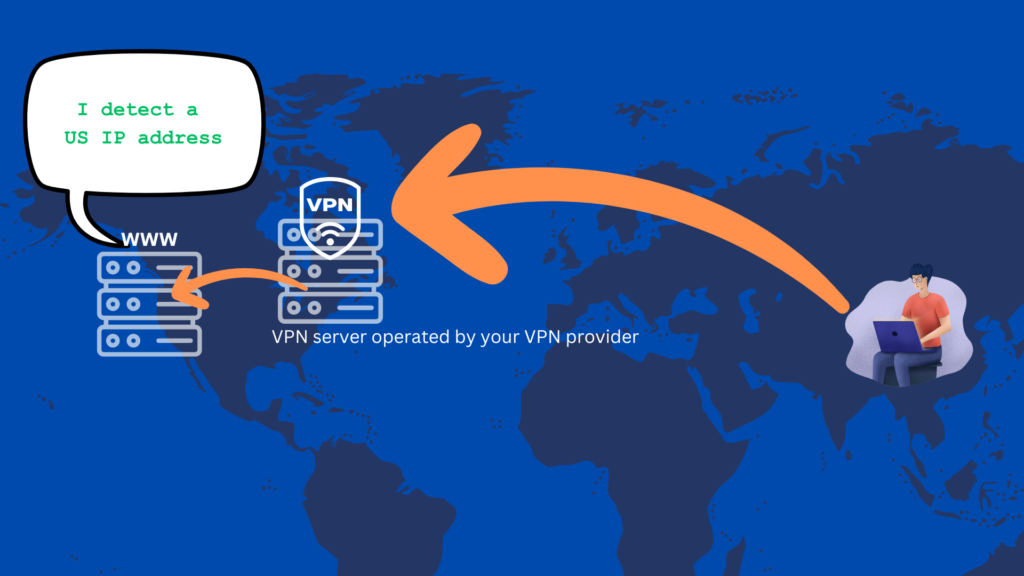
Aside from architecture, VPNs can also be classified in terms of the protocol they use. Let’s now discuss the types of VPN protocols.
Types of VPNs, Based on Protocol
A protocol is simply a shared set of rules that devices or applications adhere to in order to communicate with one another. For example, if two VPN gateways or a VPN client and a VPN server need to establish a VPN connection, they need to support the same VPN protocol. In the following subsections, we’re going to talk about the most commonly used VPN protocols today and in the past.
IPSec VPN
Internet Protocol Security or IPSec is the most widely used VPN protocol in business environments. If you want to be really technical about it, IPSec isn’t just one protocol. Rather, it’s a suite of protocols that each contribute security functions like authentication, data integrity, encryption, etc.
Due to its popularity in business environments, an IPsec VPN is a logical option for interoperability purposes. One caveat is that IPSec VPNs are normally difficult to configure. That issue gets worse if you have to deal with several VPN clients. If you’re going to use it for a site-to-site VPN, it shouldn’t be a problem. A site-to-site VPN has to be configured at only two points, the two VPN gateways. Your IT team should be able to handle that task easily.
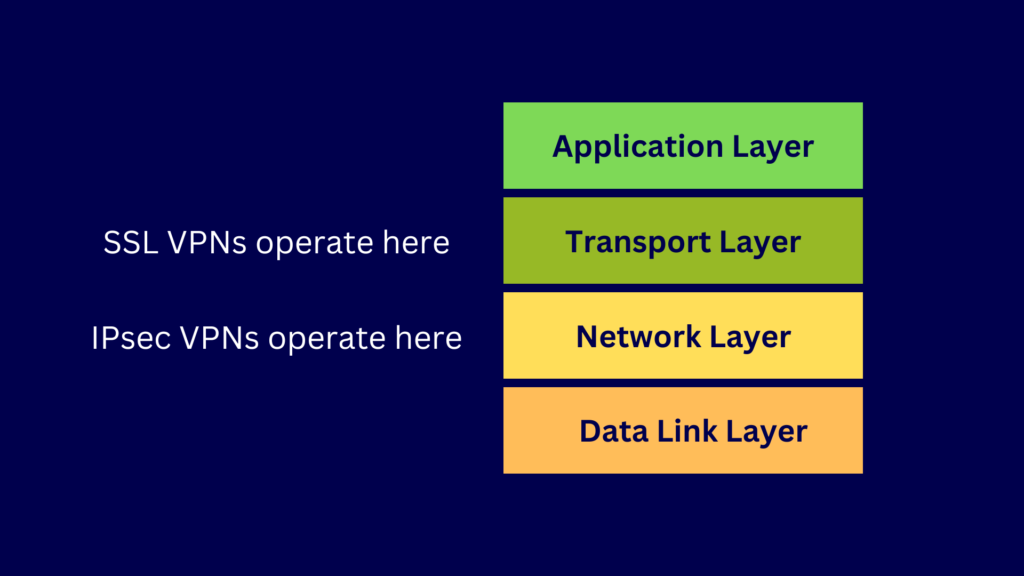
SSL VPN
SSL VPN is an overarching term that refers to types of VPNs that provide security at the transport layer of the TCP/IP model. For comparison, IPsec VPN secures at the network layer. The Secure Sockets Layer protocol a.k.a. SSL has long been rendered obsolete due to its serious vulnerabilities. So, although they’re called SSL VPNs, most SSL VPN deployments no longer use SSL. Instead, they use SSL’s more secure successor, Transport Layer Security (TLS) protocol.
Some SSL VPN implementations use a gateway-to-gateway architecture. However, these implementations are comparatively rare. In most cases, you would implement SSL VPN in a remote access-type architecture. When you use SSL VPN in this architecture, users can access your internal resources through any popular web browser.
OpenVPN
OpenVPN is arguably the most popular SSL VPN implementation. It’s open source. Meaning, it’s supported by an open community of developers and other contributors. OpenVPN is one of the few SSL VPNs that support site-to-site architecture. It also supports remote access architecture.
OpenVPN comes in two editions: OpenVPN Community Edition and OpenVPN Access Server. The former is free, while the latter is not. You can leverage OpenVPN’s community to seek assistance, find examples, and even discover projects that extend OpenVPN.
SSTP VPN
Secure Socket Tunneling Protocol VPN or SSTP VPN is a SSL VPN developed by Microsoft. It was Microsoft’s response to the growing popularity of SSL VPNs in the mid 2000’s. SSTP only supports remote access architecture, which Microsoft calls “point-to-site”.
SSTP uses port 443. Since 443 is the same port used by HTTPS, you’ll rarely encounter firewall-related issues with this type of VPN. Also, since SSTP is already included in Windows installations, your Windows users can easily enable it on their device.
PPTP VPN
Point-to-Point Tunneling Protocol (PPTP) is an older VPN protocol also developed by Microsoft. Like SSTP, it ships with Windows, which explains why PPTP was so popular in the past. Some businesses still use it to this day, but I wouldn’t recommend it. The main protocol PPTP uses for authentication, MCHAP, is found to have serious vulnerabilities. Similarly, the RC4 keys, which is used for encryption and decryption, can be easily obtained through a man-in-the-middle attack.
Because of its security vulnerabilities, PPTP is now considered obsolete. While you may try PPTP for educational purposes, you shouldn’t use it in any production environment. If you do, your passwords and data will be at risk of getting compromised.
L2TP VPN
Layer 2 Tunneling Protocol (L2TP) is yet another tunneling protocol used for implementing a VPN. L2TP was supposed to replace PPTP and, like PPTP, shipped with leading operating systems. LT2P by itself doesn’t have security mechanisms. Rather, it’s usually paired with IPsec to acquire encryption and data integrity capabilities. So, technically speaking, L2TP VPNs are actually L2TP/IPsec VPNs.
Like PPTP, L2TP has its own share of vulnerabilities that make it unsuitable for production environments. In its Special Publication 800-77 Rev.1, the US National Institute of Standards and Technology (NIST) considered L2TP and PPTP as “obsoleted and deprecated VPN protocols”.
Now that you know the common types of VPNs, let’s put that knowledge to practical use.
How to Choose the Right VPN for Your Organization
Familiarity with the different types of VPNs can come in handy when choosing a VPN for your business. Here are some basic steps you can follow to pick the right VPN.
1. Identify your specific needs
How do you intend to use your VPN? Is it supposed to provide secure network access for remote workers? Or do you want to establish a secure connection between a branch office and your HQ network? If your intention is for the former, then you’ll need a remote access VPN. If it’s the latter, then you’ll need a site-to-site VPN.
Knowing your specific need can already narrow down your options. For instance, if what you need is a site-to-site VPN, then IPsec and OpenVPN are going to be your top choices. The other VPNs can’t be used for this architecture.
2. Identify your risk appetite
How much risk are you willing to take when sending traffic over a public network? If you’ll be transmitting highly sensitive data, you can’t afford to use an obsoleted VPN protocol. If you’ll be providing remote access to highly sensitive servers, a VPN with serious vulnerabilities shouldn’t be an option. That means, PPTP and L2TP are out.
3. Identify your administrative capabilities
Do you have sufficient inhouse talent to deploy, manage, and maintain a highly complex VPN infrastructure? If not, IPsec might not be a good choice. Is your IT team comfortable with open source solutions or would they prefer something that’ already built into the Windows OS? If the answer is the latter, then you might have to remove OpenVPN from your short list.
Once you’ve ironed out these key critiera, you can then start considering less critical factors like cost, interoperability, technical support, ease of use, and so on.
I believe covered we’ve covered a lot already. Let’s wrap things up.
Final Words
In this article, we discussed the different types of VPNs. We classified VPNs, first in terms of architectures and then in terms of protocols. For VPN architectures, we talked about remote access, site to site, and host to host. For VPN protocols, we talked about IPsec, SSL VPN, OpenVPN, SSTP, PPTP, and L2TP.
Lastly, we gave a few tips to help you choose between the different types of VPNs. Some popular VPNs are already plagued with serious vulnerabilities, so it’s best to avoid those. Also, you need to consider factors like interoperability, ease of use, and cost.
In case you enountered any questions along the way, I suggest you check out the FAQ and Resources sections below. You might just find some answers there.
FAQ
What is a VPN service?
A VPN service is a VPN infrastructure managed by a third-party service provider. Some VPN services are free, but the more advanced and capable ones charge a monthly or annual fee. A VPN service is ideal if you wish to avoid the capital outlay that comes with owning a VPN infrastructure.
What is a No-Log VPN?
A no-log VPN is a VPN that doesn’t store traffic logs. This practice is done for privacy purposes. Some countries, like Switzerland, have laws that don’t allow servers to store log traffic. A no-log VPN helps VPN-equipped businesses meet that mandate.
WARP vs VPN, which is better for online security?
WARP is a cloud-based service offered by web performance and security company Cloudflare. Like a VPN, WARP protects your privacy. However, it’s not as secure as a full-fledged VPN. WARP is more focused on speed than on privacy.
Why should you use a VPN if you’re working remotely?
A VPN can keep you safe when you’re connected to a public wifi. It gives you secure remote access to files, applications, and other resources in your corporate network. In addition, it gives you anonymity by hiding your real IP address.
What VPN services would you recommend for small business?
There are several good VPN services for small businesses. Some of the best options include Kerio Control, VyprVPN, CyberGhost VPN, ExpressVPN, and NordVPN.