Knowing when an intrusion is underway is crucial to cybersecurity initiatives, as it gives you the opportunity to investigate and conduct an appropriate response. Many companies use an Intrusion Detection System (IDS) as the de facto tool for this purpose. Now, if you’re still not sure what an IDS is or have no idea how it works, you don’t have to look any further.
In this post, I’m going to explain what an IDS is, what it does, how it works, how it detects intrusions, what benefits it offers, and so on. Once you’re done reading, you’d have gained enough information to take the next step, whatever that may be in your case.
Let’s start the ball rolling by answering the question: What is an IDS?
What is an IDS?
An Intrusion Detection System or IDS is a security-oriented appliance or software application. Its main purpose is to detect intrusions, log event data, and send alerts. You can configure an IDS to store the data locally, send it to a logging server, or forward it to a SIEM. Once your IT administrator or security staff receives the alerts, he/she can analyze the data and correlate events to determine if a threat is indeed underway.
When you purchase an IDS solution, chances are you’ll find it has several components. Let’s go over them one by one.
Typical IDS Components
Generally speaking, IDS solutions come with one or more sensors or agents, management servers, database servers, and a console.
IDS Sensor or agent
An IDS sensor or agent is the part of your IDS that you would deploy on a network or host to monitor network or host activity. Sensors are usually associated with tools that monitor wired or wireless networks. Agents, on the other hand, are associated with tools that monitor endpoints or hosts. Depending on your IDS tool, you may have to deploy one or more sensors or agents.
Management server
An IDS management server is responsible for collecting data from sensors and agents. The management server can also correlate and analyze the collected data. You’ll find that some IDS solutions have one or more management servers, while others don’t have any at all.
Database server
An IDS database server is where you’ll store the event data recorded by your IDS sensors and agents. Depending on how your IDS is designed to store data, you may use an embedded database or an external database like MySQL Oracle, or MS SQL.
IDS Console
The IDS console is where you’ll perform administrative or management tasks. Depending on the console’s supported capabilities, you can use it for configuring sensors/agents and/or for conducting monitoring and analysis.
Having encountered the term multiple times now, you might be wondering: What is an intrusion? Let’s get that question out of the way once and for all.
What is an Intrusion?
In the context of cybersecurity, an intrusion happens when an unauthorized entity manages to enter your network or host. That entity can be a threat actor deliberately infiltrating a system with harmful intentions. It can also be a non-malicious but nevertheless unauthorized entity who may have simply entered the system unintentionally.
An IDS can help prevent both undesirable cases from happening by alerting security staff, who can then take preventive action. Before any prevention can take place, the IDS must be able to detect the intrusion first. To do that, IDS solutions employ one or more intrusion detection methods, which we shall go over now.
How Does an IDS Detect Intrusions?
Older IDS solutions usually relied on a single intrusion detection method — pattern-based detection. Today, IDS solutions combine multiple methods to increase their chances of detecting threats and to reduce false positives. What then is pattern-based detection and what are the other detection methods out there? Let’s go over them one by one.
Pattern or signature-based intrusion detection
Pattern or signature-based intrusion detection looks for patterns in network traffic or files and compares them with similar threat-related patterns in their database. The method is similar to the way traditional antivirus software detects malware. Once a match is found—meaning, a potential threat is detected—the IDS generates an alert.
Anomaly-based intrusion detection
Anomaly-based intrusion detection usually employs machine learning (ML) technology to create a baseline signifying safe or normal network traffic or files. Once the IDS detects a deviation from normal behavior, the anomaly is interpreted as a potential threat, and the IDS throws an alert.
Policy-based detection method
In policy-based detection, the IDS compares traffic or files against a set of pre-configured security policies, much like a firewall. The policies are usually drawn up beforehand by someone from your IT/security team or built into the IDS by the IDS vendor. Once certain traffic is found to violate policy, an alert is generated.
How Does an IDS Work?
An IDS works by monitoring inbound and/or outbound traffic and detecting intrusions through any of the detection methods I mentioned earlier. That is, by pattern or signature-based intrusion detection, anomaly-based intrusion detection, and/or policy-based intrusion detection. Once an intrusion is detected, a corresponding alert is sent.
Remember that all the IDS does is detect an intrusion, log the event, and send a corresponding alert. It doesn’t act on a threat even if it detects one. It’s up to your IT admin or security staff to confirm the presence of the threat and act on it. If you prefer a device that acts on the intrusion without human intervention, read about Intrusion Prevention System (IPS).
It might help you visualize how an IDS works if I showed you where it monitors traffic. Normally, an IDS,or more specifically, an IDS sensor, is deployed in the following manner:
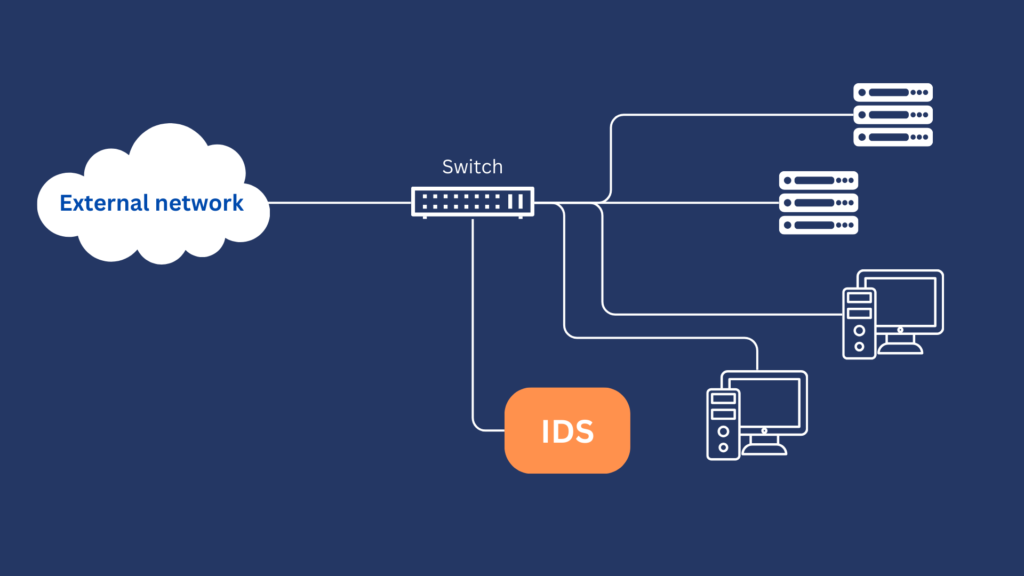
The deployment you see above is called an out-of-band or passive mode deployment and is usually implemented by connecting the IDS to a spanning port of a switch. A spanning port is a feature in certain switches that copies packets and directs them to a target interface. In this case, the spanning port directs packets to an IDS. As soon as the IDS receives the duplicate packets, it applies its intrusion detection processes on them.
The diagram above only applies to a network-based intrusion detection system (NIDS), which is arguably the most commonly used type of IDS. More about NIDS and other IDS types later. In the meantime, let’s discuss the benefits of using an IDS in general.
Benefits of an IDS
You can use an IDS to detect several threats as well as alert your security staff, who can then take appropriate action. You can gain several other benefits as well. Here are some of them.
Detects DDoS attacks
Distributed Denial of Service (DDoS) attacks can crash servers and cause considerable downtime. By conducting network behavior analysis, an IDS can identify a DDoS attack and notify your security staff. Your security staff can then reconfigure your firewall to block packets involved in the attack.
Helps meet regulatory compliance requirements
Some data privacy/protection laws and regulations explicitly or implicitly recommend the use of IDS/IPS. PCI DSS, for example, requires the use of intrusion detection techniques to detect network intrusions. Needless to say, you can meet the requirement by deploying an IDS.
Detects network reconnaissance
Network reconnaissance is the act of running tests against a network to discover potential vulnerabilities. It usually precedes most hacking attempts, as it lets the hacker understand the “lay of the land”. You can employ an IDS as part of a layered defense to identify potential network reconnaissance activities and have a threat analyst investigate IDS log data indicating such activities. That way, you can catch a hacking attempt before it escalates.
As mentioned, the IDS we illustrated earlier was a network-based intrusion detection system or NIDS. There are other types of IDS as well. Let’s briefly talk about them now.
What are the Different Types of Intrusion Detection Systems (IDS)?
There are mainly four types of IDS:
- Network-based Intrusion Detection System (NIDS)
- Wireless Intrusion Detection System (WIDS)
- Host-based Intrusion Detection System (HIDS)
- Network Behavior Analysis (NBA) IDS
It’s important you distinguish one from the other because they have certain nuances in how they’re deployed and what they inspect. This table summarizes the key differences.
| IDS Type | Deployment | What it inspects |
| NIDS | NIDS sensors are deployed out-of-band a.k.a. passive mode. See diagram above for reference. | Wired network traffic |
| WIDS | Depending on their design, WIDS sensors can be deployed using the following options: Fixed in strategic locations in your facilityInstalled on mobile devices (e.g., laptops, phones, or specialized mobile devices)Built into a wireless Access Point (AP)Built into a wireless switch | Wireless network traffic |
| HIDS | HIDS agents are installed on endpoint devices or hosts, like PCs or servers | Application-generated log files, changes to the registry, system processes. |
| NBA IDS | NBA IDS sensors are deployed inline | Sometimes network packets, but usuallynetwork flow information generated by routers and other network devices |
Final Thoughts
The goal of this article was to answer in an easy-to-digest but comprehensive way the question “What is an IDS?”. As you now know, an intrusion detection system or IDS is a tool that detects intrusions and sends alerts. We didn’t stop with that definition though.
We also talked about common IDS components like IDS sensors/agents, management servers, database servers, and the IDS console. We also discussed IDS detection methods like pattern/signature-based, anomaly-based, and policy-based detection. We even delved into the details of how an IDS works, what benefits it offers, and the different types of IDS.