Not all organizations have the time and in-house talent to fend off cyber attacks. For instance, you probably don’t have cybersecurity staff who can analyze logs, identify threats, and perform incident response. If you have that limitation, you can get a security solution to accomplish some of these tasks for you. One solution many businesses employ is an Intrusion Prevention System or IPS.
In this post, I’m going to explain what an IPS is, what it consists of, how it works, what benefits it provides, and more. You can use this information as a jump off point for further research, whether it be for educational or business-related purposes. Let’s start by answering the question, “What is an IPS?”
What is an IPS?
An Intrusion Prevention System or IPS is a security solution offered as a physical appliance or a software application. Some intrusion prevention systems are integrated into other security tools like a next generation firewall (NGFW), while others are sold separately. The main purpose of an IPS is to detect intrusion attempts, log event data, send alerts, and block potential threats.
When you purchase an IPS solution, chances are you’ll find it has several components. Let’s go over those components one by one.
Typical IPS Components
Generally speaking, IPS solutions come with one or more sensors or agents, management servers, database servers, and a console.
IPS Sensor or agent
An IPS sensor or agent is the part of your IPS that you deploy on a network or host so it can monitor network or host activity and carry out intrusion prevention. A network based intrusion prevention system sensor, for example, can block suspicious traffic. Sensors are usually associated with tools that monitor wired or wireless networks. Agents, on the other hand, are associated with tools that monitor endpoints or hosts. You may have to deploy one or more sensors or agents.
Management server
An IPS management server is responsible for collecting data from sensors and agents. The management server can also correlate and analyze the collected data. You’ll find that some IPS solutions have one or more management servers, while others don’t have any at all.
Database server
An IPS database server is where you’ll store the event data recorded by your IPS sensors and agents. Depending on how your IPS is designed to store data, you may use an embedded database or an external database like MySQL Oracle, or MS SQL.
IPS Console
The IPS console is where you’ll perform administrative or management tasks. Depending on the console’s supported capabilities, you can use it for configuring sensors/agents and/or for conducting monitoring and analysis.
You’ve already encountered the term multiple times in this article by now, so you might be wondering: What is an intrusion? Let’s get that question out of the way once and for all.
What is an Intrusion?
In the context of cybersecurity, an intrusion happens when an entity gains unauthorized entry into one of your networks or hosts. While that entity is oftentimes a hacker or malware deliberately infiltrating a system, it can also be a non-malicious person. When one of your users accidentally strays into a system where that user doesn’t have access rights for, that incident can also be considered an intrusion.
You can use an IPS to prevent both undesirable cases from happening. Your IPS can automatically detect intrusions as well as execute preventive measures on its own. So, how can your IPS detect intrusions? Let’s talk about that.
IPS Detection Methods
IPS detection is usually based on one or more intrusion detection methods. These methods include pattern-based, anomaly-based, and policy-based intrusion detection. All three were already discussed in the article “What is an IDS?”. So if you want to know more about those methods, I encourage you to click that link.
Once you’re done reading how IPS detection works, or if you just prefer not to, perhaps you’d like to know how an IPS works. That’s up next.
How Does an IPS Work?
An IPS monitors network traffic and then uses intrusion detection methods to detect potential threats. That said, an IPS doesn’t stop at detection. It also automatically blocks perceived threats upon detection. As we discussed earlier, it’s the IPS sensors that will do the blocking.
In order for an IPS sensor to perform any blocking, it has to be deployed inline as shown below. If you notice, the IPS sensor is facing the external network. An IPS sensor has to be deployed in this manner because it has to be in the path of incoming traffic in order to block threats it detects. Any packet tagged a threat by any of the intrusion detection methods is automatically blocked.
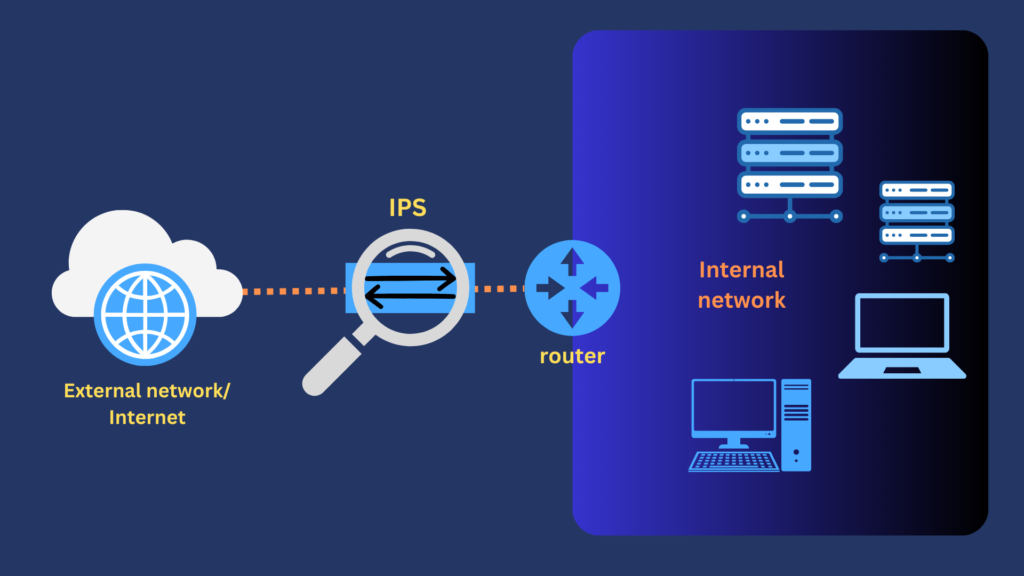
If you review the diagram, the malicious packets are blocked before they can reach the internal network behind the IPS sensor. Technically speaking—and assuming the IPS is configured perfectly—no intrusion would have taken place. Yes, the threat may have already intruded into the zone where the IPS sensor is located, but not the zone behind it. Hence the term ‘intrusion prevention’.
In a way, IPS’ auto-blocking feature gives it a significant advantage over an IDS. The diagram above only applies to a network-based IPS (NIPS), which is arguably the most commonly used type of IPS. More about network based intrusion prevention system and other IPS types later. In the meantime, let’s discuss the benefits of using an IPS in general.
Benefits of an IPS
Most of the benefits you’ll get with an Intrusion Detection System or IDS can also be acquired through an IPS. The ability to detect DDoS attacks and network reconnaissance as well as achieve regulatory compliance, for instance, can also be had with an IPS. That said, because an IPS automatically prevents an intrusion, it comes with a few additional benefits.
Automatically blocks threats
Some security solutions, most notably an IDS, only detects and alerts you of a potential threat. It can’t prevent that threat from infiltrating your systems. In most cases, detection and alerting won’t be enough. With an IPS, you’ll be less susceptible to intrusions because it’s going to automatically block a perceived threat upon detection.
Reduces security staffing requirements
An IDS can’t be effective if you don’t have security staff who can analyze IDS logs, identify potential threats from the logs, and perform incident response. Because an IPS can act on its own, detecting and blocking potential threats automatically, its staffing requirements isn’t as steep.
Frees up your security team
Assuming you have a dedicated security team, an IPS can free your team members from threat analysis and incident response tasks since it can do a lot of the same tasks on its own. Your security team can simply review IPS activity and focus more on other risk mitigation efforts.
When we were talking about how an IPS works, we were only focusing on one type of IPS—a network based IPS. There are actually different types of intrusion prevention systems.
What are the Different Types of Intrusion Prevention Systems (IDS)?
There are mainly four types of IDS:
- Network-based Intrusion Prevention System (NIPS),
- Wireless Intrusion Prevention System (WIPS),
- Host-based Intrusion Prevention System (HIPS),
- and Network Behavior Analysis (NBA) with IPS functionality.
It’s important to distinguish one from the other because they have certain nuances in how they’re deployed and what they inspect. Here’s a brief comparison between the four types.
| IPS Type | Deployment | What it inspects |
| NIPS | NIPS sensors are deployed inline. See diagram of network based IPS above for reference. | Wired network traffic |
| WIPS | Depending on their design, WIPS sensors can be deployed through the following options: Placed in strategic locations in your facility as fixed appliancesInstalled on mobile devices (e.g., laptops, phones, or specialized mobile devices)Built into a wireless Access Point (AP)Built into a wireless switch | Wireless network traffic |
| HIPS | HIPS agents are installed on endpoint devices or hosts, like PCs or servers | Application-generated log files, changes to the registry, system processes. |
| NBA/IPS | NBA/IPS sensors are deployed inline | Sometimes network packets, but usuallynetwork flow information generated by routers and other network devices |
Final Thoughts
In this post, we discussed the basic concepts of intrusion prevention systems. We started by defining an intrusion prevention system in the section ‘What is an IPS?’. We then proceeded to talk about IPS detection methods, how an IPS works, the benefits of an IPS, the different types of IPS, and other related concepts.
This introductory guide should help you easily understand more advanced content on the subject. If you’re on the lookout for an IPS tool for your business, this article should be able to provide all the basic concepts you need prior to making an informed decision.