Appearing in 25% of all attacks encountered by respondents of the 2022 VMware Global Incident Response Threat Report, lateral movement can no longer be ignored. Unless you understand what it is, how it works, and how to detect and prevent it, this malicious tactic can undermine the security of your network. We’ve got all that covered and more in this article. First, what is lateral movement?
What is Lateral Movement
Lateral movement is a tactic that many threat actors use after gaining initial access into your organization. It involves navigating across your organization’s network and breaking into your endpoints. Threat actors resort to this tactic if the initial compromise isn’t the main objective. Lateral movement is also brought into play if your attacker wants to open up alternative entry points in case you somehow manage to uncover the initial compromise.
Although some attackers deploy malware to aid in lateral movement, most prefer to “live off the land”. Living off the Land (LOL) is an evasion technique that involves using system utilities and tools readily available in a compromised endpoint.
Let’s say for example, the compromised system is a Windows host. The attacker may use PowerShell, regsvr32.exe, WMI, and other binaries found in a typical Windows installation.
The purpose of this strategy is to be as stealthy as possible. Known malware can trigger signature-based antivirus solutions. By using built-in system tools, an attacker can run a query or access another endpoint without raising an alarm. Many security solutions and analysts will just dismiss those actions as part of normal operations.
Highly sophisticated attacks that take days or even months to complete usually involve lateral movement. Lateral movement, a.k.a. east-west movement, often goes undetected and unimpeded. Why is that? Well, in the past, threats were thought to originate outside the organization. Because east-west traffic is caused by people and other entities internal to the organization, they’re considered harmless.
That’s why most of your security controls like your firewall and IDS/IPS are configured to focus more on north-south traffic, not east-west traffic.
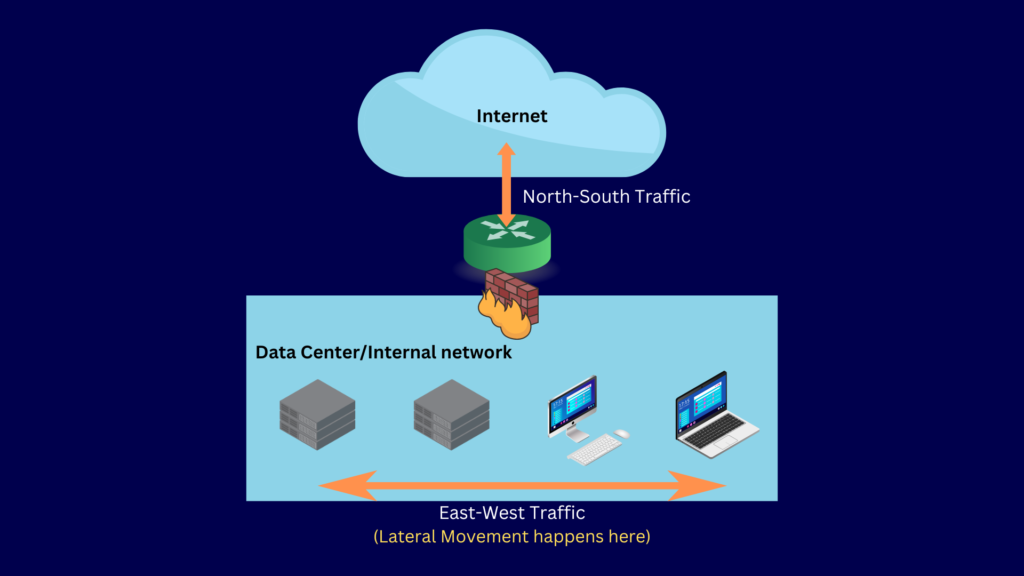
Now, however, we know lateral movement is one of the key tactics employed in modern cyber attacks.
What types of attacks use lateral movement?
Any cyber attack that benefits from having an ever greater number of compromised systems uses lateral movement. Here are some cyber attacks that employ this kind of tactic.
Ransomware attacks
Ransomware is a type of malware that encrypts files and displays a note demanding ransom payment. To increase their chances of getting paid, ransomware operators try to infect as many IT assets as possible. Some ransomware types even attack backups. To capture multiple assets, advanced ransomware variants are architected to move laterally and self-propagate.
Advanced Persistent Threats (APTs)
APTs are highly sophisticated attacks often backed by nation states. These attacks are designed to conduct extensive espionage, data theft, or sabotage. For this reason, APT operators want to keep the attack hidden for as long as they can. A typical attack can remain undetected for weeks or months. Throughout the attack, APT operators will conduct a substantial amount of lateral movement and break into multiple systems.
Botnet infections
Botnets are networks of zombified devices like servers, PCs, and even IoT devices. Once infected with botnet malware, these devices will then be at the beck and call of the botnet operators. Botnets can, for instance, be made to carry out DDoS attacks. A botnet’s strength is highly dependent on its size. As such, botnet operators try to ensnare as many devices in a network as possible. Lateral movement helps in achieving that goal.
To gain a deeper understanding of lateral movement, it would help to know how threat actors go about with it. Let’s now discuss the most common stages involved in this tactic.
Common Stages of Lateral Movement
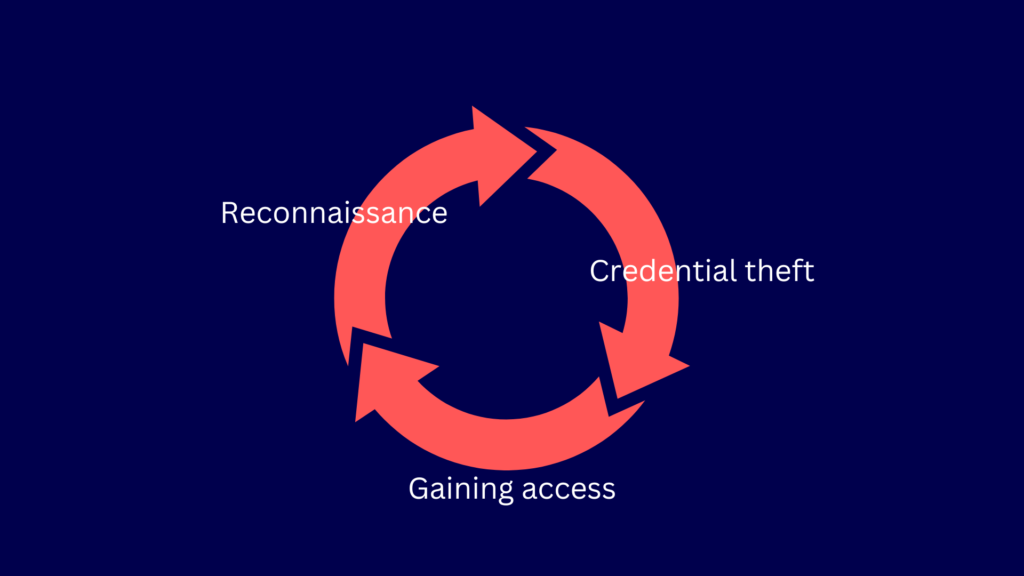
Lateral movement occurs after the initial compromise, which is attained through phishing attacks, malware infections, and other methods. After the initial compromise, your attacker will perform east-west movement in three main stages.
1. Reconnaissance
Before anything else, your attacker will want to get the lay of the land. At this stage, your attacker’s objective is to know more about your organization, hosts, network, security tools, domains, endpoints, and so on. The information gathered will help your attacker strategize for subsequent stages. For instance, by knowing your weaknesses, your attacker can choose the most suitable method for stealing login credentials.
2. Credential theft and privilege escalation
At this juncture, the objective of your attacker will be to obtain valid login credentials like usernames and passwords. Your attacker will target accounts with higher privileges than the one it currently has. Your attacker can achieve this through several methods, including pass the hash, man-in-the-middle attacks, social engineering, and others. Some attackers also use tools specially designed for stealing passwords from keystrokes and memory like keyloggers and Mimikatz.
3. Gaining access
Once your attacker obtains login credentials for an endpoint other than the one it’s currently logged into, it can then move on to that endpoint. It’s at this stage where your attacker literally moves laterally. Upon gaining access to that next endpoint, your attacker will go through the same set of processes and stages. The attacker will keep repeating these actions until the main target endpoint is breached and the ultimate objective is achieved.
Alright, so we know lateral movement is stealthy. Is there any way to detect it?
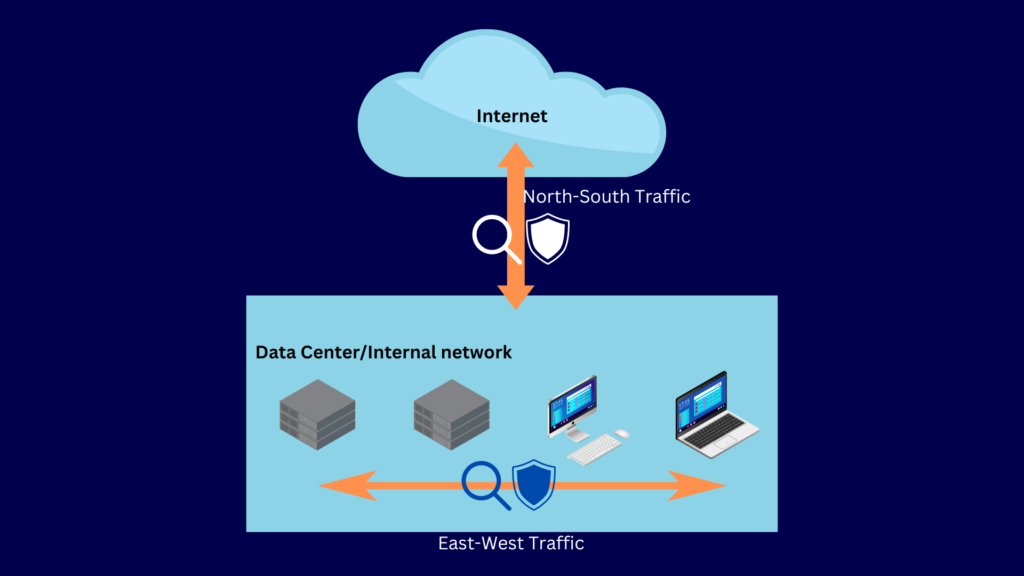
Best Practices for Detecting Lateral Movement
Lateral movement often manages to evade detection for two reasons:
- Organizations simply lack security controls for east-west traffic, and
- It often involves stolen legitimate accounts.
That said, there are a couple of best practices you can bring into play.
Update antivirus/antimalware software
If the lateral movement is carried out by a known malware, it should be detectable by robust antimalware tools. However, antimalware software need updating. The reason to update isn’t just because you don’t want the antimalware software to be compromised. Another reason is that you want its selection of malware signatures to include those of the latest malware.
Every time an antimalware vendor discovers a new malware, the vendor creates a signature for it. However, that signature will only be available in the latest update. If you want to be sure your antivirus software is capable of detecting the latest network-hopping malware, patch regularly!
Deploy solutions that use behavioral analytics
As you now know, lateral movement often involves stealing credentials associated with legitimate accounts. Some of those accounts even have administrative privileges. As such, lateral movement is hard to detect. Most security tools can’t distinguish malicious intent in what might seem like routinary action conducted by a legitimate account.
That said, a malicious action can still manifest subtle but nevertheless anomalous behavior. That anomalous behavior can trigger tools equipped with behavior analytics. If you deploy behavior-based security tools, you can have a leg up against threats that carry out east-west movement.
Detection is good, but prevention is better. Fortunately, there are several best practices for preventing lateral movement.
Best Practices for Preventing Lateral Movement
There are several ways to prevent lateral movement. Bear in mind though, no single best practice can completely prevent lateral movement on its own. As always, it’s best to take a multi-layered defense strategy and apply multiple best practices for optimal results.
Implement patch management
Aside from using stolen credentials, many threat actors do east-west movement by exploiting a system’s known vulnerabilities. Known vulnerabilities are often shared in hacking forums in the dark web. Software updates usually include security patches that fix these known vulnerabilities.
So if you patch regularly, you can counter threat actors that move laterally through vulnerability exploits. Not all vulnerabilities are known or easily found though. For those obscure vulnerabilities, you’ll need to employ more advanced tactics like penetration testing.
Perform penetration testing or hire an ethical hacker to do it for you
Some vulnerabilities are only evident to people who think like an attacker. Since you’re likely not a hacker yourself, one option is to hire ethical hackers to do penetration testing. Penetration testing is a tactic cybersecurity professionals employ that involves the same techniques used by threat actors.
Penetration tests can help you discover vulnerabilities undetectable by regular vulnerability scanners and other security tools. You can then fix those vulnerabilities and render them ineffective for lateral movement.
Institute Zero Trust Security
As mentioned earlier, the misperception that threats mainly originate from outside the network is why you often see an unequal application of security controls. Compared to north-south traffic controls, east-west traffic controls are usually much more lenient. This inequality can be corrected by adopting Zero Trust Security.
Zero Trust Security is a cybersecurity philosophy that considers all users, devices, and other entities untrustworthy by default. Meaning both north-south and east-west traffic should receive the same level of restrictions. Moreover, Zero Trust incorporates several stringent security best practices, including the principle of least privilege, strong authentication, and others. By adopting this philosophy, you’ll make it difficult for threat actors to move across the network as well as carry out privilege escalation.
Establish endpoint security
It’s not enough to monitor and secure east-west traffic. We know that lateral movement also involves compromising endpoints like servers, PCs, laptops, switches, IoT devices, etc. For this reason, it’s important to establish endpoint security as well.
Endpoint security is the practice of securing endpoints through a combination of threat prevention, detection, and response mechanisms. The most basic form of endpoint security is an antivirus. For even better protection, you can employ an EDR, MDR or an XDR solution. These security solutions offer comprehensive detection and response capabilities for endpoints and, in the case of MDRs and XDRs, other IT assets.
Apply network segmentation
A network where all endpoints can freely communicate with one another is the perfect environment for lateral movement. As long as the attacker has all the right privileges, hopping from one endpoint to another should be fairly easy. The question is—do all your endpoints really need to communicate with one another?
If not, then you should apply network segmentation. Network segmentation is the practice of splitting up your network into segments. For example, you can create segments for each business unit. Another strategy is to isolate critical IT assets from non-critical systems. Your goal is to contain east-west movement to the affected segment in the event that a system is compromised.
Alright. Time to wrap things up.
Final Words
Most sophisticated cyber threats like ransomware and APT involve lateral movement. It’s a tactic that allows threat actors to navigate deep into your network, capture as many endpoints as possible, and establish alternative entry points. It consists of 3 main stages: reconnaissance, credential theft, and gaining access.
To improve your ability to detect lateral movement, you need to update your antimalware and deploy behavior analytics solutions. You can prevent lateral movement by implementing patch management, performing penetration tests, instituting zero trust, establishing endpoint security, and applying network segmentation.
Should you have any additional questions, feel free to check out the FAQ and Resources sections below.
FAQ
What type of solution should I be looking for if I want to detect lateral movement through behavior analytics?
User and Entity Behavior Analytics (UEBA) is the class of security solutions that specializes in detecting threats using behavior analytics. Although there are solutions that specialize in UEBA, there are several other security solutions like IDS/IPS and SIEM solutions that have this capability built-in.
How do you mitigate the risk of lateral movement in a data center?
There are several security controls you can apply in a data center that can help prevent lateral movement. You can deploy firewalls, IDS/IPS solutions, multi-factor authentication, and antimalware solutions, to mention a few. Our article on data center security has a more detailed discussion on the subject.
Aside from HTTPS, SFTP, and FTPS, what are my other options against MITM attacks?
You can use a VPN. A virtual private network (VPN) can encrypt your connections like HTTPS, SFTP, FTPS, and other encrypted protocols. One big advantage of using a VPN is that it protects applications that don’t use encrypted network protocols.
What is a DDoS attack?
A Distributed Denial of Service (DDoS) attack is an attack designed to overwhelm a network’s resources with the intention to slow or even shut down the network. Once a network is overwhelmed, users can’t access its services. Many IPS solutions can identify a DDoS attack and block traffic associated with the attack.
Can firewalls help secure IoT devices?
Yes, certain types of firewalls address security issues that involve IoT devices. In fact, some Next Generation Firewalls (NGFWs) have built-in features enabling IT admins to create firewall rules based on IoT traffic.