Buying a firewall is no trivial matter, especially for a small business with a limited budget. Chances are, the firewall you decide to buy will be your first line of defense. So, not only would you want to get the best value for your money, you want that firewall to be really effective too.
In this post, you’re going to learn how to buy a firewall the right way. I understand you can’t have just any firewall that’s out there. As a key decision maker or IT manager of a small business, you’re likely facing a number of constraints large enterprises aren’t bothered with. That’s why I’m going to tailor this ‘how to choose a firewall’ article just for you.
Before you do anything else, do you know why you’re buying a firewall in the first place? What does a firewall do? Let’s get that out of the way first.
1. Know What You’re Buying – What Does a Firewall Do?
Generally speaking, a firewall inspects packets and determines, based on a set of rules, whether to allow those packets to pass or to block them. Those sets of rules can be defined by you or, in the case of a modern firewall, by security experts from the company that built it. But why is the capability of allowing and blocking packets important?
It’s important because some of those packets might be malicious in nature. They might be scanning your network for open ports to exploit. They might be carrying malware. There are many possible ways a threat actor can use the network to gain access to your systems. Hence, malicious packets need to be identified and prevented from entering.
Some malicious packets can originate from within your network as well. This can happen when, say, one of your hosts is already infected with malware. That malware may attempt to connect to its Command and Control (C&C) server. A C&C is a server that malware transmits stolen data to or receives commands from.
While the ability to block both inbound and outbound threats is the main reason why you would buy a firewall, there are non-security-related reasons as well. You can also use that ability to block unnecessary or unwanted traffic. This will enable you to avoid network congestion and maintain optimal network performance.
Now that we’ve established what a firewall does and why you would need one, it’s time to proceed with the next steps that will help you how to choose a firewall for your business. There are many factors to consider. Some of them rely on specific firewall features, so let’s talk about those features first.
2. Understand the Main Features of a Firewall
Different types of firewalls have different sets of features, but let’s start with the most basic features that popular firewalls have. When you buy a firewall, there’s a good chance it will already have these features included.
Packet filtering
Packet filtering is the most basic feature you’ll ever find in a firewall. It inspects packet header data and compares it with the firewall’s set of rules to determine whether the inspected packet should be allowed or denied entry. A firewall that can only do packet filtering is affordable, fast, and efficient. However, it’s not enough to counter sophisticated cyberthreats. You may use it to isolate mission-critical hosts from the rest of your network. However, you shouldn’t rely on it to secure your entire network.
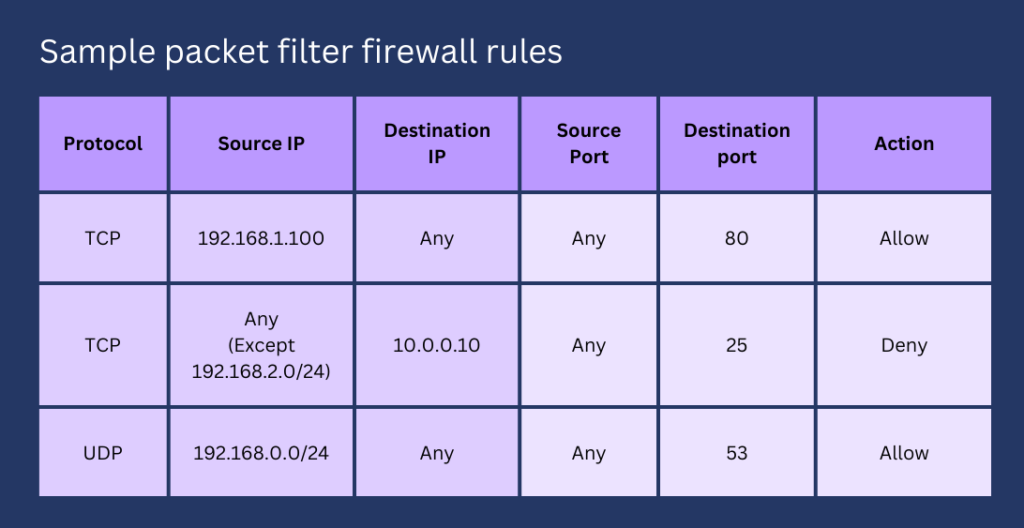
Stateful inspection
Usually working in tandem with packet filtering, stateful inspection records packet header data to determine the state of a connection. This enables it to, for instance, determine whether or not a packet is part of an open connection. If it isn’t, the packet may be deemed suspicious and blocked. Because firewalls that do stateful inspection can dynamically open and close ports based on the state of a connection, you can use it to reduce your exposure to threats that target open ports.
Router functionality
Some firewalls have built-in router functionality (and vice versa, some routers have firewall functionality as well). Meaning, aside from being able to filter traffic, they can also direct traffic to where they’re supposed to go. However, if you have several hosts behind that firewall, I would recommend you use a dedicated router for routing traffic.
Now that you’re familiar with common firewall features, let’s talk about features that are nice to have and worth your consideration when buying a firewall.
3. Understand What Other Features are Worth Considering
In the previous section, I only focused on the most basic firewall features. You can’t do a lot of protection if you only rely on those capabilities. If you’re looking for the best small business firewall for your organization, you should look beyond the basics. Here are other firewall features you should be looking for when you buy a firewall.
Deep packet inspection
Deep packet inspection (DPI) inspects not only packet headers but also their payloads. Proxy firewalls and Next Generation Firewalls (NGFWs) are the types of firewalls that support this capability. In NGFWs, the DPI module usually works in tandem with the intrusion detection system/intrusion prevention system (IDS/IPS) module to identify viruses, worms, and other malware. Because those threats can be really disruptive and even destructive, you’ll want to buy a firewall that supports this capability.

DDoS Protection
Massive Distributed Denial of Service (DDoS) attacks can disrupt your business operations and prevent your users from getting through (see FAQ below for more details). DDoS protection is a feature designed specifically to mitigate these types of attacks. If you have a public-facing service and can’t afford it to be unreachable to customers/users, this is one feature you need to seriously consider.
VPN
Virtual Private Network or VPN functionality uses encryption to protect network connections from eavesdroppers or man-in-the-middle attacks (see FAQ for more information). If you have several users (e.g., remote workers or satellite office workers) connecting to your network through the Internet, a firewall with VPN capability can be pretty useful.
Email spam filtering
Spam emails aren’t only a nuisance, they can also be harmful if they link to malicious sites. Some firewalls readily support email spam filtering, which can detect spam emails and prevent them from reaching your users’ inbox. When left unchecked, spam emails can fill up users’ inboxes in no time and can even increase the risk of malware infections. That’s why I would recommend you look for this feature when you choose the best small business firewall for your company.
Web filtering
Web filtering prevents users from visiting malicious websites. You need this capability because users usually can’t tell if a site is malicious or not. If they land on a malicious site, they could end up downloading malware or (unwittingly) sharing personal data. If you ask me, I would rank email spam filtering and web filtering on the same level of importance.
IDS/IPS
A key feature in most Next Generation Firewalls (NGFWs), IDS/IPS or Intrusion Detection System/Intrusion Prevention System uses pattern matching, anomaly-based, heuristics-based and other detection methods to discover indicators of threats in packet information and behavior. You can use this advanced feature to detect potential threats that might be able to evade traditional firewall features such as packet filtering and stateful inspection.
SSL/TLS encryption/decryption
SSL/TLS encryption/decryption is a feature that allows a firewall to decrypt SSL/TLS-encrypted connections, inspect their contents, and then re-encrypt them as they pass through. You can use this feature, which is available in most NGFWs, to automatically inspect and detect malicious content that might be hiding in encrypted connections.
Malware scanning
Here’s another feature you’ll often find in NGFWs. Malware scanning is designed specifically to detect malware in network connections. By detecting malware at the network level, you can prevent them from infecting your hosts and other endpoint devices inside your network.
In choosing the best small business firewall for your organization, it’s not enough to choose based on features. As I indicated earlier, there are several other factors to consider. Let’s talk about those other factors now.
4. Take Into Consideration Other Factors
As a key decision maker of a small business, you should be looking at several criteria before buying a firewall, not just features. How much does it cost? What is the size of your organization? Do you require remote access? These are just some of the questions you’ll have to ask before you buy a firewall. Let’s discuss these factors in more detail.
How much does it cost?
The price of a firewall can range from a few hundred dollars to a couple of hundred thousand dollars. Yes, that range is pretty broad. But once you have a budget ready, it should be easier to narrow down your list.
Just remember that you should also factor in the potential costs of getting hit by a cyber incident. How much could you end up spending if you suffer from a data breach, a ransomware attack, or a lengthy downtime due to a DDoS attack? You should factor those in too before limiting yourself to a particular price range.
What is the size of your organization?
The size of your organization can help you determine a suitable throughput (more on this in the FAQ) for your firewall and even the firewall type. For example, let’s say your small business is at the higher end of the spectrum in terms of user population. If so, you’ll probably want a firewall that can handle a relatively large network traffic or high throughput.
Another reason to consider the size of your organization is because, if you have a small population, you have the option to choose a software-based firewall. Software firewalls are installed on endpoint devices. However, if you have a big organization with a large number of endpoint devices, you should go for a hardware-based firewall. Our article on the different types of firewalls can give you an idea on how these two types differ.
What are your top cybersecurity threats?
The primary purpose of a firewall is to defend your network against cyber threats. However, not all cyber threats that are out there can impact your network as much as they would other networks. Hence, you should pick a firewall that’s effective against your biggest threats. Here are a few examples to illustrate what I mean.
DDoS attacks
DDoS attacks (see FAQ below for more details) are a bigger threat to networks that host mission-critical services. For example, let’s say you have a public-facing file transfer server in there that supports all your electronic business transactions. If that server becomes inaccessible, your main business operations could grind to a halt. That’s completely unacceptable.
Thus, because a DDoS attack can render that server inoperable, you should consider choosing a firewall that has DDoS protection capabilities. However, the same argument won’t apply to a network that’s not directly connected to the internet or that doesn’t have any mission-critical service running in it.
Data loss
Will you be storing or processing a large number of sensitive data behind that firewall? If that network holds intellectual property information or data covered by regulations like HIPAA or PCI DSS, you’ll need some kind of Data Loss Prevention (DLP) mechanism. A DLP can detect sensitive data and prevent them from leaking out of your network.
Because firewalls are usually positioned at the entry and exit points of your network, they are ideal for providing DLP functionality. If you deal with a lot of sensitive data, a firewall with DLP features is definitely worthy of consideration..
Man-in-the-Middle attacks AND malware hiding in SSL/TLS connections
Man-in-the-middle attacks (see FAQ for details) can put sensitive data such as usernames and passwords at risk. If you have reason to be concerned about these attacks, you can use SSL/TLS to secure your network connections.
However, there’s a hitch. An ordinary firewall won’t be able to inspect SSL/TLS-encrypted packets. Other threat actors can abuse this firewall limitation by hiding malware and C&C communications in those encrypted packets. You can address both threats (the MITM and the encrypted malware) by using a firewall that’s capable of encrypting/decrypting SSL/TLS connections, inspecting the content, and then re-encrypting before sending it along.
Ransomware
Now here’s one threat that can inflict severe damage in any kind of network. Ransomware can cause serious downtime as well as data loss (by way of file corruptions). What’s more, the incidence of ransomware attacks has been quite high lately. So, from a risk perspective, ransomware poses a very high risk to businesses.
Firewalls that are equipped with DPI, email spam filtering, web filtering, IDS/IPS, and malware scanning, are your best bet. Wondering how to choose a firewall that can mitigate the risk of a ransomware attack? Pick one with these capabilities.
What does your internal network look like?
The diversity of your internal network can also influence your choice of firewall. If your network consists of a broad array of devices and platforms, it might be unrealistic to choose a software or host-based firewall. Remember that most software firewalls are platform-dependent. A firewall built for Windows may not support Mac, Linux, iOS, or Android devices. In fact, a firewall built for a Windows desktop might not run on a Windows server.
Do an inventory of your IT environment. If it has a high degree of diversity, you might want to consider choosing a hardware-based firewall. A hardware-based firewall won’t care what kind of devices or operating systems you have running behind it.
Do you require remote access?
If you have to support remote workers and other users that require remote access, you must remember that these users could be vulnerable to MITM attacks. While forcing users to stick with SSL/TLS-protected network protocols such as HTTPS can mitigate this risk, there’s another option. You can choose a firewall with built-in VPN functionality. As mentioned earlier, a VPN will also encrypt data.
How much throughput do you need?
Throughput, which is usually expressed in Mbps or Gbps, is a measurement denoting how much traffic can flow through a firewall per unit time. The higher a firewall’s throughput, the faster traffic can flow through it. Generally speaking, fast throughputs equate to higher price tags, so that’s something you need to consider.
Also, the throughput indicated on a firewall’s datasheet is usually measured with all security features disabled. The actual throughput is going to be much lower than that. Specs like NGFW throughput, SSL-VPN throughput, AV throughput are more accurate, as these measurements are for when those respective features are enabled. You should remember that firewalls act as chokepoints or bottlenecks in the network. So you really need to factor in throughput when buying a firewall.
Does your firewall vendor provide good customer support?
Sooner or later, your firewall is going to have technical issues. Some of those issues might be too difficult for your designated IT guy to resolve. Some issues can even occur in the dead of the night.
Thus, you need to make sure your firewall vendor has a capable customer support team who can help you out whenever you need technical assistance. If possible, look for 24/7 support if your business operates around the clock, as you’ll never know when your firewall is going to fail or how long it’s going to be down.
5. Choose the Best Firewall for Your Business
Different businesses have different requirements—even for buying something as seemingly mundane as a firewall. Your budgetary requirements, the threats you face, the composition of your internal network, and so on, can be completely different from those of other small businesses.
Thus, there are no hard and fast rules dictating what should be the best firewall for small businesses. There’s no such thing as a one size-fits-all firewall for small businesses. Rather, you should look at different factors to determine the best firewall for your business. Hopefully, the previous sections in this article have helped you in that regard.
The Bottom Line
Knowing how to choose a firewall is something every small business IT leader must learn before setting out to buy a firewall. In this article, you were introduced to all the basic and salient points you need to consider before making a purchase.
You learned about the main motivation for buying a firewall, some basic and advanced firewall features, as well as several factors to consider. I hope you can use the knowledge you gained today to inform your buying decision.
As you read through the article, you probably encountered some unfamiliar terms and concepts. See if you can find them in the FAQ and Resources section below.
FAQ
What is SSL/TLS?
SSL/TLS stands for Secure Sockets Layer or Transport Layer Security (TLS), which are technologies that protect various application layer protocols such as HTTP and FTP using encryption. Encryption protects data by making them unreadable. SSL is the older technology and TLS is the current one, but most users keep using the acronym SSL as it’s still more widely known.
What is a C&C?
C&C or C2 stand for command-and-control. These are servers that malware communicates with to send exfiltrated data or to receive commands from. Some of these communications take advantage of HTTPS and other protocols encrypted with SSL/TLS to remain undetected.
What is a DDoS attack?
A Distributed Denial of Service or DDoS attack is a network-based attack that’s designed to overwhelm the target’s computing resources. These attacks can slow your network down and prevent legitimate users from connecting to your services.
What is a man-in-the-middle attack?
A man in the middle attack is a cyber attack where a threat actor intercepts a connection and attempts to extract sensitive data such as usernames and passwords. Network protocols that send unencrypted data are vulnerable to this type of attack.
What is ransomware?
Ransomware is a kind of malware that locks up files or even entire systems by encrypting them and then displays a message demanding ransom. The ransom note usually warns that, should the victim fail to pay at a designated time, the files will be forever encrypted. It’s currently the biggest malware threat out there.